By Lionel Snell
Editor, NetEvents
There has been, and there will continue to be a whole lot of discussion in ITC circles about how to manage the explosion (or should we say tsunami?) of devices that are forming the Internet of Things (IoT). Little wonder, because this particular explosion is barely controlled by the IT industry – so much of it is arriving left field from other business sectors.
Previous big, impactful explosions – personal computers, networks, smartphones, the Cloud etc – have been created and driven by IT. The industry was responsible for persuading people to buy these products and responsible for building and delivering them. But in the case of IoT the industry is offering as much a service as a product – and there is a whole population of devices out there just waiting to be fitted with chips and connected to the IoT. Sell a PC or smartphone and you are selling a complete package that complies with a host of regulations and standards, but sell 5G connectivity and you may not be certain if it is for a medical device, for tracking containers, for a utility meter, a drone controller or whatever.
So the IT industry is feeling anxious about opening wide the Internet to a vast population of newcomers. Kevin Restivo, IDC’s Research Manager, European Enterprise Mobility led a conference session at NetEvents EMEA IT Spotlight entitled They’re Everywhere! Managing the Incredible Explosion of IoT and IIoT Devices. His introductory presentation was summed up in the figure below: “Framing the market – that’s what we do IDC. We size, forecast markets, describe the drivers and inhibitors. At IDC we believe IoT is one of the fastest growing markets or collection of technologies relative to the ICT spectrum”.
“First and foremost, what does IDC mean by the Internet of Things? … It is a network of uniquely identifiable endpoints… that autonomously connect bidirectionally using IP connectivity. The ecosystem is really a complex mix of technologies and services… server, storage, analytics, IT services, security and a range of other technologies… essentially a wide span of the ICT spectrum”.
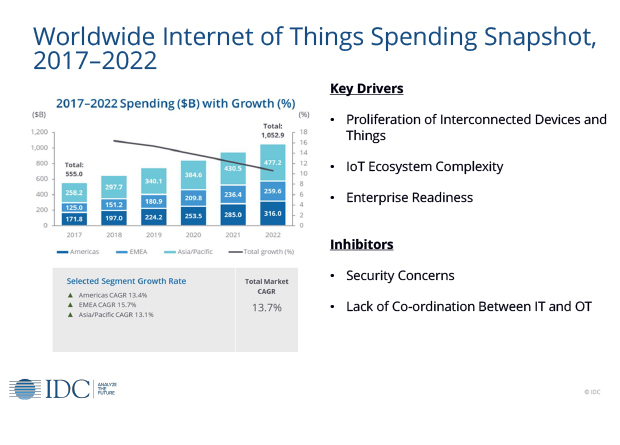
This diversity makes it harder to pin down the elements of spending, he explained. Up till now, about a third has been on IoT devices and similar amounts on software and services. But in the future forecasts he expected much more spending on analytics, as business begins to extract value from its IoT and optimize its processes.
As to drivers: obviously the explosion of devices is a major factor, but complexity might sound more like an inhibitor, until you consider the vast array of systems and protocols involved: “That complexity is driving a lot of spending”. The third driver, Enterprise Readiness, reflects that almost limitless population of devices and systems already out there and waiting to get connected.
As to the inhibitors, lead by security fears, he explained: “Lack of coordination between operations and IT is very much an inhibitor to deployment. Close collaboration between IT and operational departments is necessary and yet it doesn’t happen. Everyone wants to protect their fiefdoms or they’re simply not able or willing to cooperate… IT is often left behind during the project planning and budgeting and the piloting. That lack of coordination can really stall the successful deployment of IoT initiatives”.
After that brief sketch, Kevin, asked the panel for their views on drivers and inhibitors, but it quickly became necessary to break down the IoT into broad categories. Peter Galvin, Chief Strategy and Marketing Officer, nCipher Security, compared the fast growing consumer segment, with very little focus on security, to the Industrial IoT (IIoT) – which is “a little more thoughtful” – as well as the already highly regulated medical segment, used both by consumers and healthcare professionals.
Kevin suggested putting aside the consumer market for this session and focussing on business, government and industry. Jan Guldentops, Director, BA Test Labs, pointed out that there was still a massive difference between parking sensors – sending tiny amounts of non-critical data – and industrial systems with hundreds of sensors controlling millions of dollars worth of equipment: “It’s like cloud all over again”.
On the question of security, Philip Griffiths, Head of EMEA Partnerships, NetFoundry, said that security was the greatest inhibitor but that some organisations are actively seeking solutions: “I’m working on an engagement at the moment where a Fortune 10 company is rolling out an IoT solution. They’re not involving IT because they want to move as quickly as possible. But the partner we’re working with, who’s an ISV, came to us and said, we need to make sure the solution is very secure so that, when IT do come along, we can say ‘this is more secure than your corporate network so there’s nothing for you to worry about’. At the same time, we don’t want to have to manage 50,000 VPNs – so we’re going to use your [NetFoundry’s] solution because it automates that secure connectivity”.
Moving on to business benefits as drivers, Professor Martin Curley, Director of the Digital Academy and Open Innovation, The Health Service Executive, said we should expect a consumerization of healthcare on a scale to match the recent consumerization of IT. Referring a book with the great title The Patient Will See You Now, he suggested: “we will have patients routinely showing up to their cardiologist or to their nephrologist with much better information than the consultants themselves have. The Apple Watch with its ECG is already an FDA-regulated device. It can detect atrial fibrillation. It could be lifesaving.”
He explained that ‘vital signs’ is the term for the key predictors that nurses use to determine if a patient is deteriorating and, in a traditional manual system based on handwritten notes, over 50% of those scores can be wrong. Whereas SyncroPhi had developed a solution to automatically connect, collect and display these vital signs. He saw so many diverse opportunities in healthcare: “Another company is developing technology to track equipment in the ward. One of the key issues is there’s so much time spent by nurses and doctors looking for equipment that somebody else has borrowed. They’ve developed a smart solution that RFID-enabled tracks where the equipment is in the wards. I can probably give you 10 other examples… I think the biggest untapped market is going to be healthcare”.
Peter Galvin came up with other examples, notably industrial automation: “giant wheat harvesters out in the mid-west, there’s nobody in those. They’re all remotely controlled. They’re considered an IoT device and they’re giving telemetry data and also data about what’s the soil like? What’s the content like?” He also quoted an Australian mining company automating extremely remote and inaccessible mining sites.
Jan Guldentops quoted smart cities: how those unpopular traffic cameras, used to fine motorists, also collect vital traffic data, as do automated parking systems. Philip Griffiths doubted that smart cities was such a hot market, because it does not offer the clear revenue opportunities promised by an industrial manufacturing plant where, for example, thousands of cameras can monitor for defects in real time and save a fortune. Guldentops reponded that might be true in the US model, whereas in Europe there is serious government money available for smartening up cities.
Griffiths made an interesting point about how IoT is best sold: not so much a product sale as bringing together an ecosystem of technology providers to deliver a full turnkey stack for the end company to pay for as a service rather than assemble it themselves: “it’s fundamental to IoT because otherwise it’s far too complex to pull together as one business”. And Galvin referred back to the sheer value of data collection and collation to be analysed for scientific research that could have major applications in the future.
Michael Kagan, Chief Technology Officer, Mellanox Technologies, came up with a rather horrifying example of the importance of well-considered policies: “If I’m building the algorithm for a self-driving car I need to take into consideration the fact that if I have two bicyclists in front of me and an accident is unavoidable, how do I choose which one to hit?… One of the options can be, we’ll hit the one that wears a helmet because he has a higher chance to survive. Once this algorithm becomes known, nobody is going to wear helmets anymore because you’re going to be hit by the car if you wear a helmet… Once we make the decision, we need to figure out the implications.”
Guldentops argued that security was not really holding back IoT, simply because not enough people were considering it. For example: “A certain brand of speed cameras runs a Debian 6 operating system that hasn’t been patched since I think 2010. It takes me around three and a half minutes to become root on that system… I talked to the guys and they said, we cannot patch it because we need to validate the system and every change we make the speed camera is not valid anymore. But still there are around 400 ANPR cameras in Belgium that are using it.”
Griffiths warned of the risks when IT networks merged with industrial networks: “most of the attacks we’ve seen have been some sort of phishing campaign turning into malware, laterally moving from the IT network into the OT network because someone didn’t think about security enough, and then blowing up a billion dollar steel facility or something as happened in Germany a few years ago… If we create secure connectivity with software-defined perimeters, zero trust, all these things, then you can get the benefits of both worlds.”
Martin Curley feared that we all need some big catastrophe to wake up the industry and its customers: “Similar to the Boeing 737 Max with its angle of attack sensor – that is an internet of things device. For the IoT industry that is a road to Damascus moment, where software resilience and software validation has to be done in a much more thorough way”.
We already have these catastrophes, notably in compromised healthcare systems and Curley agreed there was severe under-resourcing: “There’s barely enough staff to just get the systems functional never mind thinking about security”.
For Guldentops, bug bounties was one of the best innovations within the security industry in the last couple of years: “you can get a community of people who like to get into your system but not break it, who do it as an intellectual challenge. So, they can report their problems, earn sometimes a living with it. It’s something we should start using in IoT. If you’re a company developing a device and you want to put it on the market, hire one of those bug bounty companies and get some people to play with it, to break it… you’ll know there’s a security problem in it before you roll it out to 10,000 people”.
The snag with this idea, especially in medical and industrial IoT is that it’s the legacy problem. As the devices are already in place bug bounties aren’t going to provide a simple solution as they either can’t be patched, or it’s inefficient to patch them, or it’s too costly to patch them.
To deal with this legacy problem Griffiths suggested overlaying the legacy system with a secure greenfield solution. Taking Guldentops’ speed cameras as an example: “How do we throw NetFoundry on there so that someone can’t get into it? They’ve still got that underlying, flaw but you at least layer over a more secure solution on that so you make it much harder for someone to get access to that and root password it”.
Michael Kagan rounded off the session by proposing the need to identify and understand the interfaces and not mix too many things together: “With the segregation of the infrastructure, computing and application it enables you to update these two tiers absolutely independently… Don’t tie things too much together, so you can update them and manage them and provision them independently”.
The transcript of the entire discussion is available at https://www.netevents.org/wp-content/uploads/2019/01/Debate-V-IoT-IDC-draft.pdf.