Kaspersky Lab researchers monitoring the various clusters of the long standing, Russian-speaking threat actor, Turla (also known as Snake or Uroburos) have discovered that the most recent evolution of its KopiLuwak malware is delivered to victims using code nearly identical to that used just a month earlier by the Zebrocy operation, a subset of Sofacy (also known as Fancy Bear and APT28), another long standing Russia-speaking threat actor.
The researchers also found target overlap between the two threat actors, centered on geopolitical hotspots in central Asia and sensitive government and military entities.
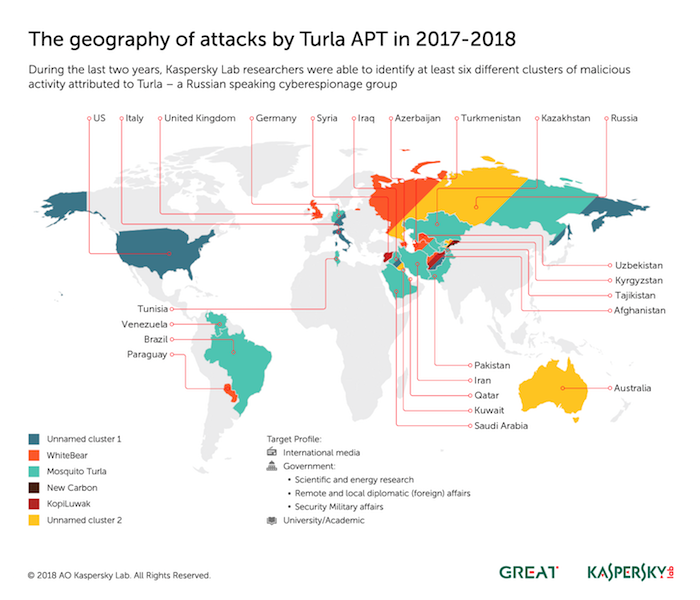
The findings are included in an overview of the latest evolution and activity of four active clusters attributed to the Turla threat actor, published today by Kaspersky Lab’s Global Research and Analysis team.
KopiLuwak (the name derives from a rare type of coffee), was first discovered in November 2016, delivering documents containing malware and with macros enabled that dropped new, heavily obfuscated Javascript malware designed for system and network reconnaissance.
The most recent evolution of KopiLuwak was observed in mid-2018, when researchers noticed new targets in Syria and Afghanistan. Turla used a new spear-phishing delivery vector with Windows shortcut (.LNK) files.
Analysis showed that the LNK file contained PowerShell to decode and drop the KopiLuwak payload. This PowerShell was almost identical to that used in Zebrocy activity a month earlier.
The researchers also found some targeting overlap between the two threat actors, focused on sensitive political targets, including government research and security entities, diplomatic missions and military affairs, mainly in central Asia.
Other Turla malware clusters tracked by the researchers during 2018 include those known as Carbon and Mosquito.
In their overview, the researchers provide further evidence to support the hypothesis that Wi-Fi networks were abused by Turla to deliver Mosquito malware to victims, a practice that may be tapering off.
They also found further modification of the mature and powerful Carbon cyberespionage framework, which has traditionally been installed only very selectively on victims of particular interest, and expect to see further code modifications and selective deployment of this malware into 2019.
The 2018 targets for the Turla malware clusters include the Middle East and Northern Africa, as well as parts of Western and Eastern Europe, Central and South Asia, and the Americas.
“Turla is one of the oldest, most enduring and capable known threat actors, renowned for constantly shedding its skin and trying out new innovations and approaches,” said Kurt Baumgartner, principal security researcher at Kaspersky Lab’s GReAT team. “Our research into its main malware clusters during 2018 shows that it continues to regrow and experiment.”
However, Baumgartner noted that while other Russia-speaking threat actors like CozyDuke (APT29) and Sofacy were targeting organizations in the west, such as allegedly hacking the Democratic National Committee in 2016, Turla was quietly deploying its operations towards the east, where their activity and, more recently, even their delivery techniques began to overlap with Sofacy’s Zebrocy subset.
“Our research suggests Turla’s code development and implementation is ongoing, and organizations that believe they could be a target should prepare for this.”
Kaspersky Lab recommends that to reduce the risk of falling victim to advanced targeted attack operations, organizations may wish to consider the following actions:
- Use a proven corporate grade security solution in combination with anti-targeted attack technologies and threat intelligence, like the Kaspersky Threat Management and Defense solution. These are capable of spotting and catching advanced targeted attacks by analyzing network anomalies, and give cybersecurity teams full visibility over the network and response automation.
- Provide security staff with access to the latest threat intelligence data, which will arm them with helpful tools for targeted attack research and prevention, such as indicators of compromise (IOC), YARA and customized advanced threat reporting.
- Make sure enterprise grade patch management processes are well established and double check all system configurations and implement best practices.
- If you spot early indicators of a targeted attack, consider managed protection services that will allow you to proactively detect advanced threats, reduce dwell time and arrange timely incident response.