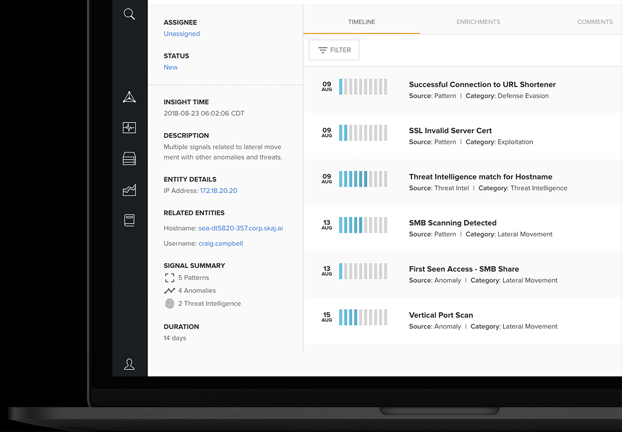
JASK, provider of the industry’s first Autonomous Security Operations Center (ASOC) platform, is capturing industry demand with new features centered around enterprise-wide alert linkages and analyst workflow efficiency. Enhancements include the JASK Navigator, a visually-driven, contextually-rich investigation console that provides SOC analysts a one-click path to situational attack awareness, multi-asset data ingestion; query flexibility and analyst team workflow support.
“Through our discussions with both partners and customers one thing has become crystal clear, the SOC of the future will not rely heavily on legacy SIEM technologies,” said V.Jay LaRosa, VP Global Security Architecture, Chief Security Architect at ADP. “There are a lot of cybersecurity solutions and technologies promising ways to get more out of technology investments, and JASK is maniacally focused on truly addressing enterprise-wide alert prioritization, context and visibility by focusing on analyst workflows.”
Since launching the platform in July 2017, JASK’s vision is delivering an asset-independent, open platform that enables an autonomous workflow of what, where, why and how analysts should take action. Using artificial intelligence (AI) and machine learning as its base engine, the platform is built for broad and smarter data ingestion to reduce costs and bandwidth without losing context. With its latest enhancements, the JASK ASOC platform improves visibility through unique mapping of data to records linked across devices, users, networks, applications and almost any third-party data source.
“JASK understands the urgency CISOs have placed on consolidating and integrating security operations technologies,” said Jon Oltsik, Distinguished Analyst and Fellow at Enterprise Strategy Group. “By seamlessly fitting into existing environments, offering an intuitive user interface and reducing the overwhelming volume of alerts, JASK is addressing the top concerns SOC teams report.”
JASK Navigator is a visually-driven investigation console that equips analysts with an actionable view of JASK Insights, prioritized notifications of data that indicate a combination of events or activities that should be investigated, with all the associated signals and alert information that led to its delivery. Investigations are streamlined and logical, offering SOC teams one-click access to better prioritized insights and faster paths to resolution.
To further support enterprise analyst workflows, JASK is also developing team support via customizable workflow queues within the ASOC platform. This allows customers to represent user groups or teams in order to assign the triage of JASK Insights. The enhanced workflows allow teams to easily adjust the Insights stage, providing improved visibility into the overall status of all assigned tasks. JASK also allows analysts to assign and visualize alerts from existing security solutions by user, team and status.
“The attacker is winning in today’s constantly changing threat landscape. The SOC is no longer human-scalable,” said J.J Guy, CTO of Jask. “A flexible platform that focuses on analyst workflows to improve efficiency is a critical step forward in offering SOC teams immediate visibility and context. We must stop building our teams to support technology, and build technology to support our teams.”
JASK doubled its customer base in the first quarter of 2018, adding enterprises spanning higher education, financial services, healthcare and retail. Additionally, the company continues to support existing security operations workflows through partnerships and specific integrations with leading solutions in cybersecurity, including Cylance, Demisto, Carbon Black, Microsoft Active Directory, Splunk, ArcSight, among many more.