Kaspersky revealed the drop in Bruteforce attacks against remote workers in Southeast Asia (SEA), a positive news that should not be taken as a sign to be complacent.
Remote Desktop Protocol (RDP) is Microsoft’s proprietary protocol, providing a user with a graphical interface to connect to another computer through a network. RDP is widely used by both system administrators and less-technical users to control servers and other PCs remotely.
A Bruteforce.Generic.RDP attack attempts to find a valid RDP login/password pair by systematically checking all possible passwords until the correct one is found. A successful attack allows an attacker to gain remote access to the targeted host computer.
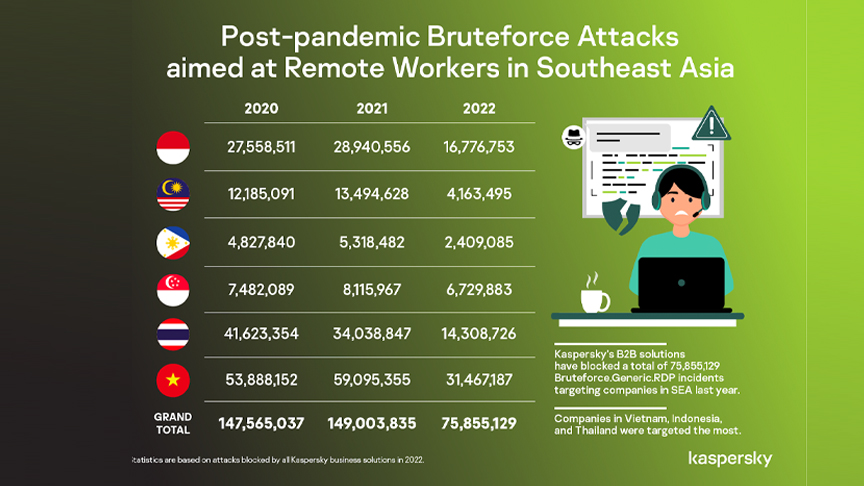
Global cybersecurity company’s telemetry showed Kaspersky’s B2B solutions have blocked a total of 75,855,129 Bruteforce.Generic.RDP incidents targeting companies in SEA last year.
2022’s total number is a 49% dip from 2021’s 149,003,835 Bruteforce attacks. The decline in quantity has been observed across all the six countries in SEA.
In terms of share of Bruteforce attacks last year, companies in Vietnam, Indonesia, and Thailand were targeted the most.
“From almost 150 million Bruteforce attacks against companies here in 2021, last year witnessed just half of them. It’s a good sign at first glance. In part, this was influenced by shifting to either a pure face-to-face or a hybrid remote environment, which means there are fewer remote workers in the region as compared to the peak of the pandemic in 2022 and 2021,” explains Yeo Siang Tiong, General Manager for Southeast Asia at Kaspersky.
“It is, however, too early for businesses to proclaim total safety from Bruteforce attacks. Looking at the wider threat landscape, our experts see more modern ransomware groups exploiting RDP to gain initial access to the enterprise they are targeting. It’s a red flag that security teams should pay close attention to,” Yeo adds.
A recent Kaspersky report unmasked the most popular techniques for gaining initial access among ransomware groups. Exploiting external remote services came up as the most common for the ransomware groups analyzed.
In fact, all of the eight ransomware groups covered in the report which are mostly operating as a RaaS (Ransomware as a Service) – Conti, PysaClop (TA505), Hive, Ragnar Locker, Lockbit, BlackByte, and BlackCat – use valid accounts, stolen credentials or Bruteforcing to get into a victim’s networks.
The report also notes all of the ransomware groups used open RDP to gain initial access to the system as this is the easiest vector for initial access.
A best practice for protecting against RDP-related attacks is to “hide” it behind a VPN and properly configure it. It is also very important to use strong passwords.
To reduce the risk and impact of a ransomware attack caused by RDP Bruteforce, Kaspersky experts also suggest deploying a comprehensive defensive concept that equips, informs and guides your team in their fight against the most sophisticated and targeted cyberattacks like the Kaspersky Extended Detection and Response (XDR) platform.
Find out more about this new platform at go.kaspersky.com/expert .
Kaspersky in Southeast Asia also has launched a Buy 1 Free 1 promo. Businesses can now enjoy two years of enterprise-grade endpoint protection for the price of 1 with Kaspersky Endpoint Security for Business or Cloud or Kaspersky Endpoint Detection and Response Optimum, with 24×7 phone support. Interested customers can reach out to sea.sales@kaspersky.com.