By Guy Matthews
Editor, NetReporter
Like it or not, the enterprise world is entering a phase of ‘digital dependence’. This somewhat sobering conclusion is drawn by Fernando Montenegro, Senior Principal Analyst, Cybersecurity Infrastructure Security Intelligence Service with analyst firm Omdia.
The recent pandemic, he says, has driven digital transformation up the corporate agenda and led to technology being more essential to business success than ever. So what has brought about this heightened level of reliance on tech?
“The first driver has been the rise of more distributed workforces, especially for knowledge workers,” he says. “The second thing is what I call fast-paced digital value chains. We’ve moved towards adopting different providers of different services across our value chains. Thirdly, transformation has led to much more distributed compute, particularly where technology is supporting physical processes in the world. We are further ahead in the deployment of 5G technology, supporting IoT use cases and industrial IoT use cases. Lastly, we have now adopted cloud-based environments almost as a default for organizations.”
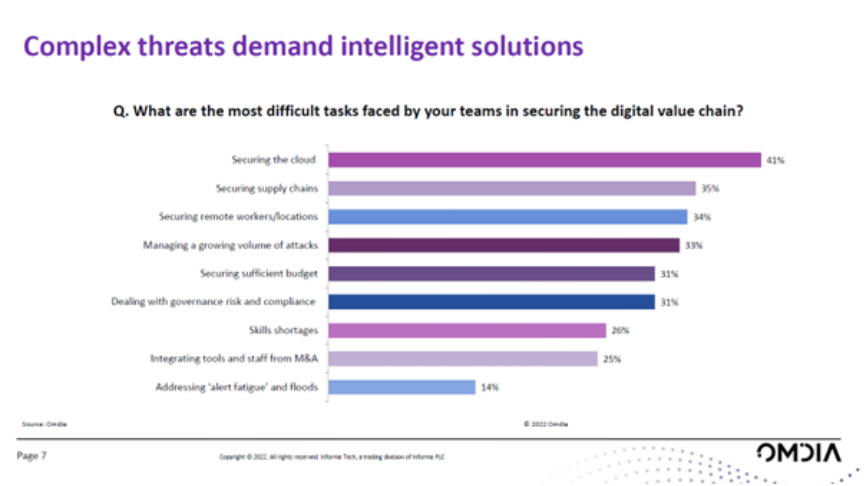
Underpinning all four of these areas is the perennial headache of cybersecurity. So what, in the context of a multitude of transformational initiatives, are the top security priorities that Omdia has uncovered in its research? Securing the cloud is perennially cited by IT bosses as their most difficult task, says Montenegro.
Figure 1: Complex threats demand intelligent solutions
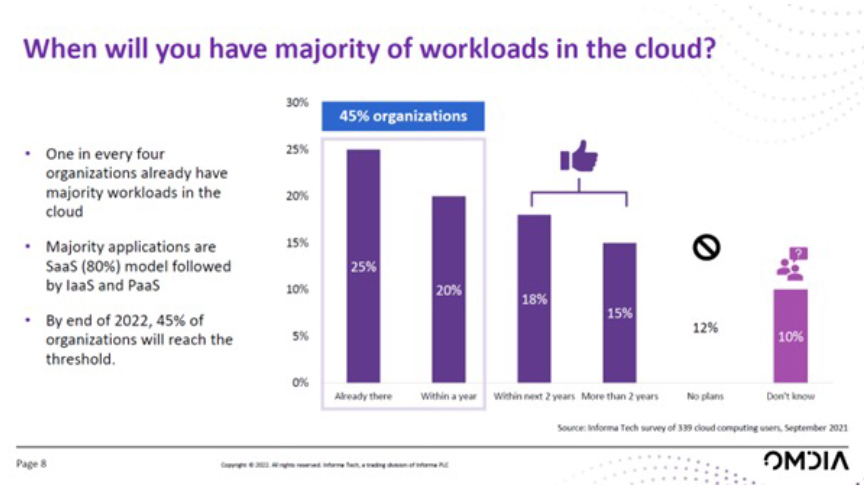
As part of its research, Omdia also sought to find out when enterprises expect to have the majority of their workloads in what they clearly see as the somewhat vulnerable environment of the cloud. It turned out that 25% have already passed that tipping point, while 20% said they would be there within the year.
Figure 2: Workloads in the cloud
So, for CIOs considering cloud adoption, along with all its attendant threats, perceived or real, what seem to be the most compelling use cases for the application of appropriate security? And what of cloud-delivered security – that is security designed to live in the cloud or be consumed as a cloud-based service? To help answer this knotty problem, Montenegro pulled in a panel of leading names in the cyber and cloud fields.
Chad Skipper, Global Security Technologist, Network & Advanced Security Business Group with vendor VMware sees lots of opportunities, not for any old security but for cloud-delivered security. He identifies two use cases, firstly traditional applications with the sort of virtualized capabilities that were commonplace before digital transformation intervened: “Now enterprises want to take those workloads and deliver them off premise in the cloud, as cloud-delivered security,” he observes. Secondly, post digital transformation, Skipper identifies ‘modern’ applications as a second use case. Think containers, think Kubernetes, think cloud applications delivered as a service.
“That’s a different delivery model because those are running itty bitty micro services within that cloud infrastructure,” he says. “The security is somewhat the same in both cases, but the insertion mechanism is different. Traditionally, you need visibility right into every packet and every process. But for a modern application, we’re talking APIs and the ability to discern what threat actors are doing once they get inside a perimeter. Once everything outside of your perimeter was considered bad and everything inside was considered good. But that’s no longer the case. And so we need to have that visibility, whether it’s in the modern applications or the traditional applications to really understand what those threat actors are doing.”
Haiyan Song, Executive Vice President and the Head of Security with security vendor F5 sees a key benefit of cloud-delivered security as the chance to deliver security where users are actually located: “When you think about federated identity, I think that’s one of the good use cases,” she claims. “You no longer have to go back to your own central identity and access management. It can be delivered in a much better and faster way, more flexibly. The other nature of cloud delivered security has something to do with the ability to correlate, aggregate and get insights from a cloud-connected world. You’re able to see what’s coming and what’s happening in the network, and apply that to the rest of the company. I think that’s one of the crown jewels of cloud-delivered security – having insights that one once analyzed, many can benefit from.”
With security going from on-prem to cloud comes the evolution of firewall services and also web application and API protection services, believes Sashi Jeyeratnam, Senior Director of Product Management for Security Solutions with security vendor Spirent. The nature of cloud, she says, is very elastic: “You have highly ephemeral workloads, and things change very quickly. You need to make sure tools have cloud awareness, and awareness of workloads. If your security solutions are not aware, then they are not going to scale very well and be effective for you.”
The main reason why people move to the cloud is because of agility, she adds: “You need to be able to embrace new workloads that are popping up and new security policies that need to scale effectively. CISOs now have a goal of making sure of business continuity. They don’t want to be seen as roadblocks.”
Also up for debate was the panel’s recommended practices for an organization that is going down the cloud-delivered security path. Regardless of where you are in your transformation journey, argues Jeyeratnam of Spirent, whether you have just one workload in the cloud or half of them, you need an end goal in mind on the journey to ensure that you make the right choices: “Having to set visibility and security controls, having tool sets that help you navigate the heterogeneous environment that your hybrid networks represent, I think that’s going to be a critical factor,” she says. “And the other thing is that with cloud, it’s all about scale.”
Song of F5 warns of the need to be mindful of vendor management at the outset: “When you deal with incident response, that’s when you depend on a third party,” she explains. “You need to have agreements in place and your drills down ahead of time, especially for business-critical applications. Consider the example of Log4J, one of the biggest cybersecurity events of last year. In order to work through that one you needed to have an agreement and protocol in place with your vendors. The other thing I would certainly advocate is always to have multi-layer defence. Nothing is perfect, but you need best practices for your venture into cloud-based security.”
Thoughts turn lastly to likely future developments in IT that will have a bearing on adoption of cloud-based security. Song of F5 summed up her considerations in three words, all starting with a D: “Everyone is becoming more and more decentralized,” she notes. “People work from anywhere, and applications need to be delivered to wherever. The second word is disaggregated. Every app uses multiple components and services and that adds more and more complexity. Thirdly, everything is going digital.”
Skipper of VMware argues that visibility is and always will be key: “How do you get all packets and processes right, especially in a multi cloud world?” he muses. “In a virtualised world, the future is going to be about data processing units, or DPUs. We’ve heard of GPUs, we’ve heard of CPUs, but look out for DPUs, also called Smart NICs. The challenge that we’ve had in the cloud operating model is when we add security we are consuming the CPU and memory of the application. Moving those security capabilities off the CPU onto a smart NIC is the future for a multi cloud operating model.”
In conclusion, Jeyeratnam of Spirent sees the future in terms of the data that is coming from the mass of cloud infrastructure in use: “How to manage that data? Some kind of AI or ML applied to it is going to be very important, so as to be able to manage the vast amount of logs and alerts that are coming down. A major trend going forward is being able to correlate that data. We need information to be able to correlate and use data to predict what a security posture might look like, or what might to go wrong. The industry is going to have to move towards being able to help organizations achieve that.”