Cybercriminals are constantly coming up with new methods to deliver their spam and phishing messages to both individuals and businesses. Armed with the knowledge of the latest trends, they take advantage of the seismic shift in digital habits during the pandemic to launch social engineering attacks such as phishing emails.
Kaspersky’s data showed that by including hot topics and phrases related to their online activities like shopping and streaming entertainment or the COVID-19 pandemic in their messages, the chances of an unsuspected user clicking infected links or malicious attachments increase tremendously.
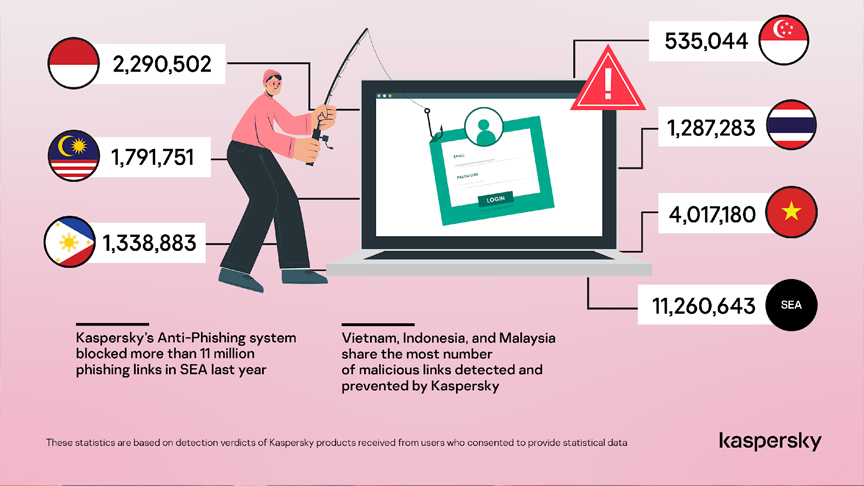
In 2021, Kaspersky’s Anti-Phishing system blocked a total of 11,260,643 phishing links in SEA. Most of it were blocked on devices of Kaspersky users in Vietnam, Indonesia, and Malaysia.
“Email remains to be our main mode of communication for work here in Southeast Asia and 11 million phishing attempts in one year is just the tip of the iceberg. With all the critical data being sent via email, it is expected for cybercriminals to see it as an effective and lucrative entry point. An unfortunate example is the $81M Bangladesh Bank Heist in 2016 which was made possible by a single, successful targeted phishing attack. Enterprises in the region should carefully look into holistic and in-depth cybersecurity technologies to beef up the security of their highly critical mail servers,” says Yeo Siang Tiong, General Manager for Southeast Asia at Kaspersky.
Globally, 253,365,212 phishing links were detected and foiled by Kaspersky solutions last year. In total, 8.20% of Kaspersky users in different countries and regions around the world have faced at least one phishing attack.
Remote work and business email compromise (BEC)
The remote work triggered more attempts to phish corporate details for the past two years. Among the rising trends is business e-mail compromise (BEC).
BEC attacks are a type of fraud that involves impersonating a representative from a trusted business. A BEC attack is defined as a targeted cybercriminal campaign that works by:
- Initiating an e-mail exchange with a company employee, or taking over an existing one;
- Gaining the employee’s trust;
- Encouraging actions that are detrimental to the interests of the company or its clients.
According to Verizon, it was the second most common type of social engineering attack in 2021, and the FBI reported that BEC attacks cost U.S. businesses more than $2 billion from 2014 to 2019.
Kaspersky experts are increasingly observing BEC attacks. In Q4 2021, Kaspersky products prevented over 8000 BEC attacks, with the greatest number (5,037) occurring in October.
Throughout 2021, the company’s researchers closely analyzed the way fraudsters craft and spread fake emails. As a result, they found out that the attacks tend to fall into two categories: large-scale and highly targeted.
The former is called “BEC-as-a-Service”, whereby attacks simplify the mechanics behind the attack in order to reach as many victims as possible. Attackers sent streamlined messages en masse from free mail accounts, with the hope of snaring as many victims as possible. Such messages often lack high levels of sophistication, but they are efficient.
An example of mass-scale CEO scam
The above message is an example of a mass-scale CEO scam scheme.
In this scenario, an employee receives a fake email from a more senior colleague. The message is always vague telling that one has a request to handle. A victim may be asked to urgently pay off some contract, settle some financial conflict, or share sensitive information with a third party. Any employee may potentially become a victim. Of course, there are several noticeable red flags in such a message. There is no corporate account used, and the sender clearly is not a native speaker.
At the same time that some criminals are relying on simplified mass mail outs, others are turning towards more advanced, targeted BEC attacks. The process works as follows: attackers first attack an intermediary mailbox, gaining access to that account’s email. Then, once they find a suitable correspondence in the compromised mailbox of the intermediary company (say, financial matters or technical issues related to work), they continue the correspondence with the targeted company, impersonating the intermediary company. Often the goal is to persuade the victim to transfer money or install malware.
An example of targeted BEC attack
Since the target is, in fact, engaging in the conversation referenced by the attackers, they are far more likely to fall victim to the scam. Such attacks have proven to be highly effective, and that’s why they’re not only used by small-time criminals looking to make a quick profit.
“Right now, we observe that BEC attacks have become one of the most widespread social engineering techniques. The reason for that is pretty simple – scammers use such schemes because they work. While fewer people tend to fall for simple mass-scale fake emails now, fraudsters started to carefully harvest data about their victims and then use it to build trust. Some of these attacks are possible because cybercriminals can easily find names and job positions of employees as well as lists of contacts in open access. That is why we encourage users to be careful at work,” comments Roman Dedenok, security expert at Kaspersky.
How can enterprises handle BEC attacks
Cybercriminals use a fairly wide range of technical tricks and social-engineering methods to win trust and carry out fraud. However, taking a range of effective measures can minimize the threat from BEC attacks:
- Set up SPF, use DKIM signatures, and implement a DMARC policy to guard against fake internal correspondence. In theory, these measures also permit other companies to authenticate emails sent in the name of your organization (assuming, of course, that the companies have those technologies configured). This method falls short in some ways (such as not being able to prevent ghost spoofing or lookalike domains), but the more companies that use SPF, DKIM, and DMARC, the less wiggle room cybercriminals have. Use of these technologies contributes to a kind of collective immunity against many types of malicious operations with e-mail headers.
- Train employees periodically to counter social engineering. A combination of workshops and simulations trains employees to be vigilant and identify BEC attacks that get through other layers of defense.
- Use security tools to protect corporate communication channels such as Kaspersky Secure Mail Gateway with a solid set of anti-phishing, anti-spam, malware detection technologies. While BEC represents one of the most sophisticated types of email compromise, the product has a dedicated heuristic model for processing indirect indicators and detecting even the most convincing fake emails.
- Subscribe to an in-depth and regularly updated threat intelligence services to have in-depth visibility into cyberthreats targeting your organization.
Kaspersky solutions with content filtering specially created in the company’s lab already identify many types of BEC attacks, and its experts continually develop technologies to protect further against the most advanced and sophisticated scams.