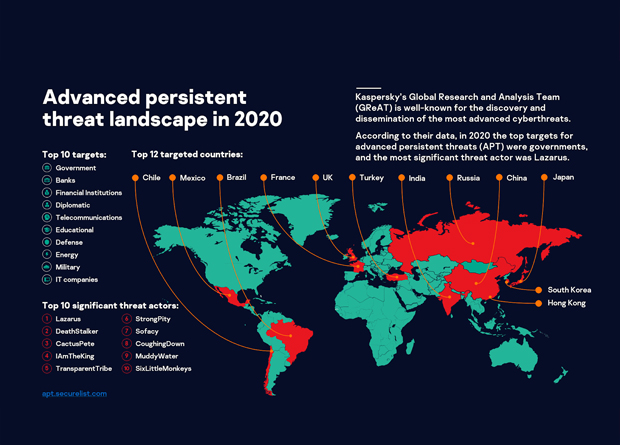
Cybersecurity firm Kaspersky disclosed that banks and financial institutions are major targets of advanced persistent threats (APTs) as the pandemic continues in Southeast Asia. Among the top 10 targets of sophisticated attacks, these industries ranked second and third and every year, they have always been ranked on the list of top targets.
Seongsu Park, senior security researcher, Global Research and Analysis Group at Kaspersky, revealed the main trends in the general cyberspace landscape in Southeast Asia which include the following: hackers attack not only Windows systems but other non-Windows operating systems as well; the use of mobile phone to steal credentials and important information; hackers focus on supply chain attacks; and exploiting Internet facing network device.
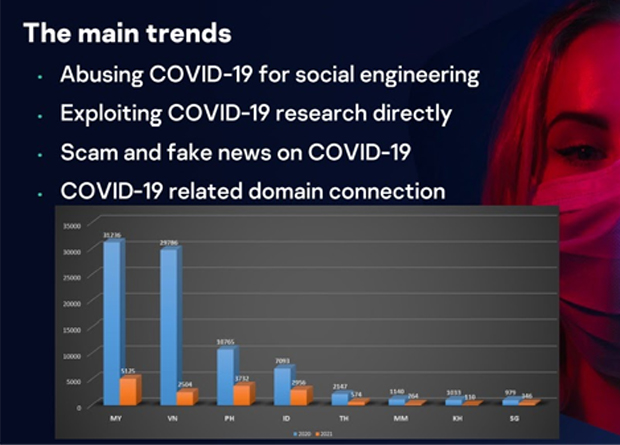
Other important trends are the use of COVID-19 theme for social engineering; exploiting researches directly related to COVID-19; scam and false news on COVID-19; and COVID-19-related domain connection which can be used for scam.
Last year, over 80,000 COVID-related domain connections and malicious websites were detected by Kaspersky in SEA alone. Malaysia registered the highest number, followed by Vietnam, the Philippines, and Indonedia.
Park cited a case using COVID-19 theme. “In December 2020, the largest group tried to steal COVID-19- related intelligence and targeted government organizations and some pharmaceutical companies to steal the 2019 information,” said Park.
This trend is expected to continue until 2021 as the region continues its battle against the pandemic and rolls out vaccines in different phases.
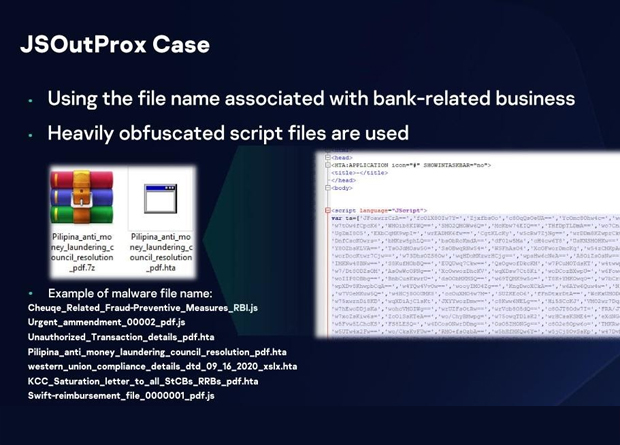
Various sectors in the financial industry are targeted by cyber attackers, especially cryptocurrency business which is a prime target these days. One of the campaigns that targeted banks (and even government agencies) in SEA is the JSOutProx malware. This malware continued its attempt of infiltrating banks in the region even though it is currently not a highly sophisticated strain.
This sophisticated malware employs social engineering tactics such as using file names associated with bank-related business and heavily obfuscated script files to get into the network. Once it runs on the victim, it can load several plugins performing additional malicious activities on the victim.
Cryptocurreny business is also the subject of cybercriminals who are undertaking online attacks on the sector. Kaspersky identified that one of the cryptocurrency exchange in the region was compromised. As a result of a thorough investigation, it was confirmed that the Lazarus group was behind the attack that was detected in Singapore.
Another cryptocurrency-related threat is the SnatchCrypto campaign conducted by the BlueNoroff APT, a subgroup of Lazarus which particularly attacks banks. It was also allegedly associated with the $81M Bangladesh Bank Heist.
Kaspersky has been tracking this SnatchCrypto since the end of 2019 and discovered the actor behind this campaign has resumed its operations with similar strategy.
In terms of the factors behind the increased threats against the sector, Yeo Siang Tiong, General Manager for Southeast Asia at Kaspersky comments, “Cryptocurrency is steadily being embraced in SEA, hence it is a natural progression for cybercriminals to set their eyes here. Its growth is part and parcel of the region’s digital transformation, and is parallel to the increased adoption of e-commerce and digital payments.”
“As we continue to move our money to the online world, we have also witnessed massive data breaches and ransomware attacks last year which should serve as a warning for financial institutions and payment service providers. It is crucial for banking and financial services providers to realize, as early as now, the value of intelligence-based, proactive defense to fend off these costly cyberattacks,” Yeo adds.
The Kimsuky APT group, which has most likely been operating since 2012, is employing spearphishing to attack its victim. A very agile and versatile APT group, this threat has a strong motivation for financial profit. It initially targeted think-tanks in South Korea, particularly for cyberespionage.