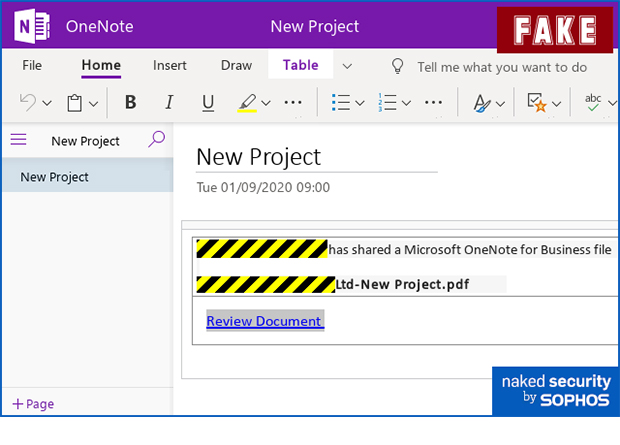
Sophos reported new phishing scams through cloud-based platforms. This involves the use of SharePoint and OneNote to go after passwords. Instead of simply spamming out a clickable link to as many people as possible, cybercriminals would use more labyrinthine techniques.
First, crooks would send an innocent-looking email with an attachment from a sender, whose email account had evidently been hacked. The attachment takes the victim to a message with a Sharepoint link to access a One Note file that leads to a login form. If the victim puts in a password, it goes straight to the crooks.
Given this new phishing scam, Paul Ducklin, Principal Research Scientist at Sophos, has provided some tips to help users and companies stay secure:
- Don’t click login links that you reach from an email. That’s an extension to our usual advice never to click login links that appear directly in emails. Don’t let the crooks distract you by leading you away from your email client first to make their phishing page feel more believable when you get there. If you started from an email, stop if you hit a password demand. Find your own way to the site or service you’re supposed to use.
- Keep your eyes open for obvious giveaways. As we’ve said many times before, the only thing worse than being scammed is being scammed and then realizing that the signs were there all along. Crooks don’t always make obvious mistakes, but if they do, make sure you don’t miss them.
- If you think you put in a password where you shouldn’t, change it as soon as you can. Find your own way to the official site of the service concerned, and log in directly. The sooner you fix your mistake, the less chance the crooks have of getting there first.
- Use 2FA whenever you can. Accounts that are protected by two-factor authentication are harder for crooks to take over because they can’t just harvest your password and use it on its own later. They need to trick you into revealing your 2FA code at the very moment that they’re phishing you.
- Consider phishing simulators like Sophos Phish Threat. If you are part of the IT security team, Phish Threat gives you a safe way to expose your staff to phishing-like attacks, so they can learn their lessons when it’s you at the other end, not the crooks.