Sophos, a global player in next-generation cybersecurity, published a report on a malware family whose infection numbers have been steadily growing since the beginning of the year. This malware has been getting regular updates and feature enhancements that seem to be focused on its ability to conceal itself from detection on infected computers.
The report took a deep dive into what makes the Glupteba malware distinctive. The core malware is, in essence, a dropper with extensive backdoor functionality, but it is a dropper that goes to great efforts to keep itself, and its various components, hidden from view by the human operator of an infected computer, or the security software charged with its protection.
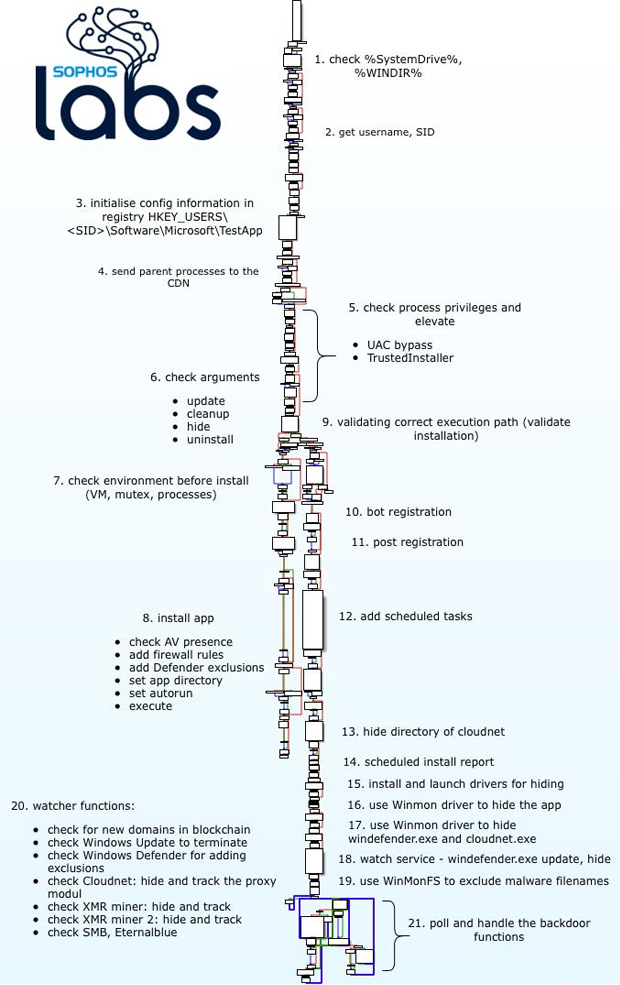
To accomplish these tasks, the creators of Glupteba have opted to take a modular approach to their malware, which can download and execute payloads intended to extend the functionality of the bot. Many of these payloads are exploit scripts and binaries that originate in open source tool repositories, like Github, and have been lifted whole-cloth from their archives to be leveraged against the victim’s computer.
One of the ways Glupteba uses these exploits is for privilege escalation, primarily so it can install a kernel driver the bot uses as a rootkit, and make other changes that weaken the security posture of an infected host. The rootkit renders filesystem behavior invisible to the computer’s end-user, and also protects any other file the malware decides to store in its application directory. A watcher process then monitors the rootkit and other components for any sign of failure or a crash, and can reinitialize the rootkit driver or restart a buggy component.
That watcher process also gets used to deliver a surprising amount of bug reporting telemetry back to Glupteba’s creator(s). After all, an application crash is a very noticeable event, and if the goal of the malware is to maintain its stealth, then avoiding crashes is of paramount importance.
The malware also uses the Windows Registry to its advantage, storing many of its configuration options under unobtrusive Registry key names. The names of some of these configuration values also provide a clue about Glupteba’s overall goals. For instance, the bot stores the name(s) of its command-and-control server(s) under a key labeled “CDN” – a term of art in the hosting industry that refers to a Content Delivery Network, a type of business that caches frequently-requested data so it can be retrieved more rapidly by a large population.
Sophos can infer that the bot’s propensity to self-protection and stealth, and this CDN label, that Glupteba’s creators intend this malware to be part of a service offering to other malware publishers, giving them a pay-per-install business model for malware delivery.
“The most unscrupulous threat actors design their malware to be stealthy. This means that they strive to stay under the radar and remain in the wild for a long time, performing reconnaissance and collecting information to determine their next move and to hone their malicious techniques. While researching Glupteba, we realized the actors behind the bot are investing immense effort in self-defense. Security teams need to be on the lookout for such behaviour. In addition, Glupteba is designed to be generic, capable of implementing a wide range of different malicious activities through its different components and extensive backdoor functions,” said Luca Nagy, security researcher at Sophos and lead author of the report.















































































































