By Scott Raynovich
Principal Analyst, Futuriom
Our sense of security is deeply ingrained. For centuries we understood that, if a house has doors, you lock them. So, if your business network has an entry point, you install a firewall. But BYOD, wireless connectivity, and cloud applications have exploded the number of entry points. In today’s connected world, every single device or application expands the attack surface. If the network periphery goes fractal, where do you put security?
The cloud has changed everything on the network. It’s changed traffic patterns, behaviors, and network architectures. Shortly, if not now, the bulk of enterprise traffic exiting the LAN will be heading for the cloud. It used to be a self-contained world of a corporate LAN or WAN. This is creating more bandwidth demand and it requires a more flexible architecture. You can’t just install a firewall – you have to have security apps distributed wherever your users are going.
Kevin Deierling is Senior VP of Marketing, Mellanox Technologies and he sees the same problem: “They used to say ‘secure the network against attacks from outside’, but more and more in the cloud model they’re coming from inside – because the cloud model invites third parties that are potentially untrusted right into the middle of your datacentre. So, that old security model of perimeter protection is not adequate. It’s still important, but it’s not adequate”.
Another rising challenge is appliance sprawl. Enterprises have racked and stacked appliances for a variety of networking applications that should be native to the network itself. In the beginning, there were a few internal switches and then a router to connect with the outside world. Now there hundreds of different kinds of devices with different characteristics and different protocols, ranging from WAN optimization to application delivery control. It’s going up the stack into the software layer: we have orchestration tools and visibility tools and so on. These are the things that network and IT managers are struggling with.
The way that the enterprise is interacting with the cloud is now changing the game. This has a vital bearing on security policy: is it MPLS or Internet? Private cloud or public cloud? Is the end users coming from a private MPLS network, business quality internet, or home broadband? For a larger organisation the picture becomes more complicated as this diagram suggests.
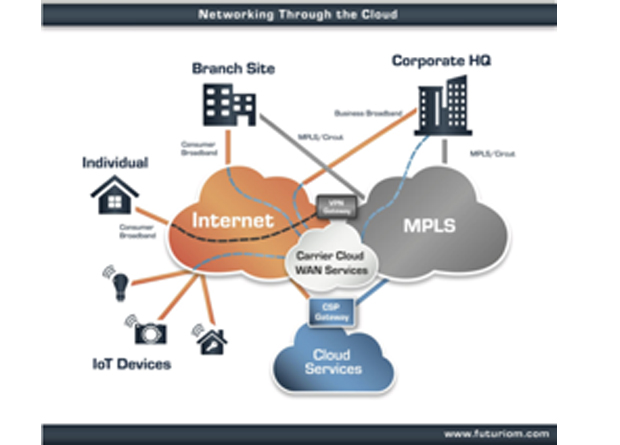
Look closer at the diagram and it begins to fragment into complexity. Kelly Ahuja, the CEO of Versa Networks points to the need for data-center segmentation in order to isolate applications that can become threat vectors, and in a branch office even the printers could be vulnerable to capture – unless, like HP Enterprise printers, they can detect and self-heal from malware.
So where should we put security? The answer is to put it everywhere: Security is going to be pervasive across every environment. The edge as we knew it, the network perimeter as we knew it, was really about the external edge. In the future, it’s going to be about internal perimeters – and everything is going to have to get protected in every possible way.
There is no shortage of security tools available, and that becomes another part of the problem. There are end-points, there is container security inside the datacentre, and firewalls at the edge. Drill down, and there are literally hundreds of tools for CISOs to look at and evaluate to attack specific problems. From the end user perspective, it’s overwhelming. It is not just about the technology now, it’s the human management problem these solutions generate: If you look at all the major breaches, whether it’s Target or Chase or the IRS or Equifax, it almost always leads back to a human error. Either there were things flagged that weren’t paid attention to, or there were decisions not to patch web servers and so it’s really an organizational issue as much as a technology issue.
The human problem must be solved with automation. And network security challenges need to be solved with native security built directly into the network.
Given such uncertainty, and so many possible leaks, encryption becomes a more interesting solution: if you cannot stop the data getting into enemy hands, you might at least make sure they cannot read it. Encryption has a key role in the traditional closed model, as Deierling explains: “Normally you have an encrypted secure tunnel from the client into the datacentre and the cloud. But once it’s in the cloud, then people assume that’s a trusted model and inside it’s not encrypted”.
But with today’s internal perimeter model you cannot seal the cloud, but is it practical to encrypt within the data center? Won’t ubiquitous encryption slow everything down? Not so, says Deierling: “We have introduced a new network adaptor product that performs encryption at 200 gigabits per second line rate. We do this for point to point encryption with Ipsec, we do it for TLS [Transport Layer Security], so that’s sort of the transport layer, and we encrypt data at rest on the hard drives. This is going to become ubiquitous… two of our major customers now adopt encryption inside of their datacentres.”
MK Palmore is a Field CSO of Palo Alto Networks and he too sees encryption as a security fundamental: “Encryption certainly has risen to the level of best practice, both for data at rest and data in transit.” Indeed its value is increasingly recognized by the general public, with nearly half the buying public recognizing its importance when buying tech devices and services – according to a Christmas 2019 survey by nCipher Security.
Kelly Ahuja agrees that encryption will happen everywhere, but how is it best delivered: “Our job isn’t to determine where encryption has got to be used. Our job is to be able to provide ability to encrypt wherever a customer needs it.” For example: “If you look at Wi-Fi 6, there is a WPA3 standard that’s coming out which has WPA3/OWE that stands for Optional Wireless Encryption. They are actually going to use encryption in the wi-fi domain.”
More contentiously, Palmore recommends hardware assist: “Clearly when you’re in a datacentre at a 200-gig interface, you do need hardware assist. If there is hardware assist available, every system should use that to do it because that’s going to give you the best performance.”
Here Deierling does not agree: “Hardware assist is extensions in the Intel CPU that can do the decryption in software and it accelerates that. However, if you look at all the other things – overlay networks, virtual machines, hypervisors that switch between the virtual machines – all of that is done in hardware today… If you use software to encrypt the packet, all those things break. All of the hardware accelerators that companies like ourselves have put into the network interface cards over the last 20 years, all break. Because when you have an encrypted connection, all of the information we need to look at – overlays, TCP/IP headers and checksums – all of it becomes encrypted because there’s a giant IPsec tunnel. We don’t see any of it. All of our accelerations break. So, I actually think [the acceleration] needs to be inline in the network adaptor.”
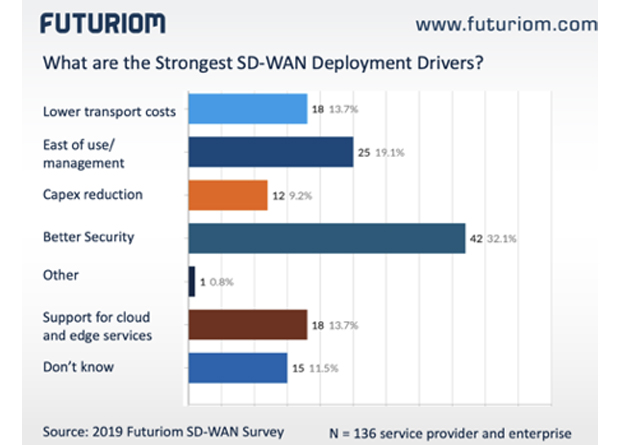
Another way to install security everywhere is as a secure overlay. Futuriom’s 2019 SD-WAN Survey asked 136 service providers what’s driving their SD-WAN implementation, and security came out way on top – see diagram.
All of these factors are driving a convergence of tools at the enterprise tools. We don’t need routers, firewalls, and WAN optimization devices anymore – we need a converged enterprise edge. SD-WAN vendors are sounding more like firewall vendors these days: talking about their security stacks and their next generation firewalls.
Palo Alto, known for its second generation firewalls, does not disagree: “Palo Alto Networks has acquired several best of breed entities over the past 18 months to align our vision of the future, and it does involve a bit of consolidation” says Palmore. “We think firewalls will remain present both in physical and virtual form, but we think firewalls should deliver a number of services to our customers… The cyber security of the future involves a tremendous amount of automation, because most enterprises cannot scale from a workforce standpoint to what’s needed in the cyber security industry… We are also doubling down on cyber threat intelligence. The idea that no one entity sees the entirety of the threat landscape but, if you use a patchwork approach and cobble together visions of the landscape, you can extract data and information that enables you to provide security services from a wide variety of sources”.
Speaking for the SD-WAN vendors, Kelly Ahuja says “When a market is hot, everyone tries to go for it.” The company’s approach has been to give the customer an option: “We’re an open platform. We can sit beside a physical Palo Alto or we can put a virtual Palo Alto VNF and service chain that together. We can do that with Fortinet, Riverbed, Silver Peak, Cisco – you name it. The key thing is to solve the customer’s problem and most of them have an existing environment where you have to fit in and enable a smooth migration. Whether they move to a cloud or stay on-prem, it’s really going to be their call and every customer is going to be different. You’ve got to have versatility, and that’s where the name Versa comes from.”
Security has to be everywhere – that is the conclusion we come away with when talking to the industry’s top experts. It needs to be a coordinated net of many approaches and that can be managed with a lot of automation.
One final point following this technology discussion: “security everywhere” must include security in the workforce. When bored, or distracted under pressure, humans can be the weakest link in the security chain. On the other hand, alert, informed and disciplined employees add up to the network’s strongest security overlay.