With the onset of the internet, social engineering attacks are not only becoming common; they are getting more and more sophisticated. Hackers are devising progressive methods to fool employees and individuals into handing over sensitive company data. With so many threats, enterprises must use due diligence in an effort to stay one step ahead of these hackers.
Let’s discuss the basics of software engineering and the different ways social engineer use to extract valuable information and how to detect them.
What is Social Engineering?
Social engineering is the dark art of manipulating people. In order to get access to a building, a piece of information they aren’t supposed to have or to blackmail people, social hackers use specific decisive methods to fool employees into revealing valuable information that can be used to gain unauthorized access to their system.
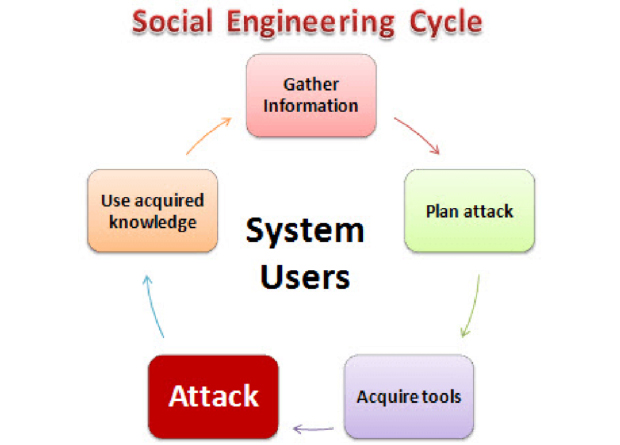
Tips for Recognizing a Socially Engineered Hack
Most of these attacks exploit the basic human emotions such a trust, kindness, greed, and curiosity. Despite developing and upgrading security software programs we, humans, have proved to be the weakest link in the information security chain. You can get help from different social engineering training courses that teach end-users how to identify and avoid leaking vital information to these hackers.
We asked a panel of security experts to uncover the most common ways these hackers use to gain information. So, to get a general idea of how to detect if you’re being set up for a hack, let’s take a look at the most common methods used.

1. UNSOLICITED TECH SUPPORT CALLS
If you get a call from someone claiming to be tech support, you are most likely being set up for hack. You should build up your defenses and try ignoring the call entirely or avoid giving away any vital data.
If they claim to be someone from within the office, you should call them up to your desk to make sure that you are not spoofed. Hackers mostly use tech support as a disguise to obtain information such as passwords, ask you to download something or direct you to a website that might infect your computer.
2. KEEP A CLOSE EYE ON YOUR EMAILS
Phishing is one of the most common online scams where hackers send you an email that appears thoroughly professional and ask you to provide sensitive information. Email scams are also a popular method to transmit malware through infected attachments or to fill out a form to extract information such as social media logins, bank account information, etc.
Hackers target specific organizations which they know are most likely to fall for these scams. There are several ways to spot a phishing email, such as;
- Watch out for the sender’s email address and its content. If it addresses general public like “Dear Customer” or “Dear Employee”, ignore it.
- Avoid any mail that contains links. You can hover over the link to see the destination and if you don’t recognize it, don’t click.
- Be wary of attachments; phishing emails often require you to take immediate action to avoid grave consequences.
- Most hackers have started to send emails with forged Password Request links. At first glance, these messages look genuine, but if you take a second look at the source URL, you will know that something is not right.
3. BEWARE OF UNPLANNED INSPECTIONS
When employees don’t fall for online scams, social engineers opt for a more direct method of hacking and often pose as IT inspectors. Visibly they give a very professional look, and their goal is to get access to restricted areas or to install malicious software onto computers within an organization.
You should always keep a keen eye on what they are doing and always check with the management to make sure that it is an authorized inspection.
The Bottom Line
If you tell your employees to keep a keen eye on their proceedings on the internet, they can detect something odd and know when someone is trying to hack them. But, in order to be fully hack free, you need to enroll your employees in a professional social training program so that when the time comes, and believe me it will come, they will be ready to shrug off a social engineer.
















































































































