In 2006, Clive Humby, a Sheffield mathematician, made headlines when he declared that ‘data was the new oil’. Though it has been a decade, the realization that there is a lot of money to be made – and lost – through the handling of big data has just begun to dawn on many business people.
Data breaches continue to be a threat to enterprises and consumers, especially in the wake of recent events here in the Philippines and across the region, such as Facebook-Cambridge Analytica and SingHealth cyber hack.
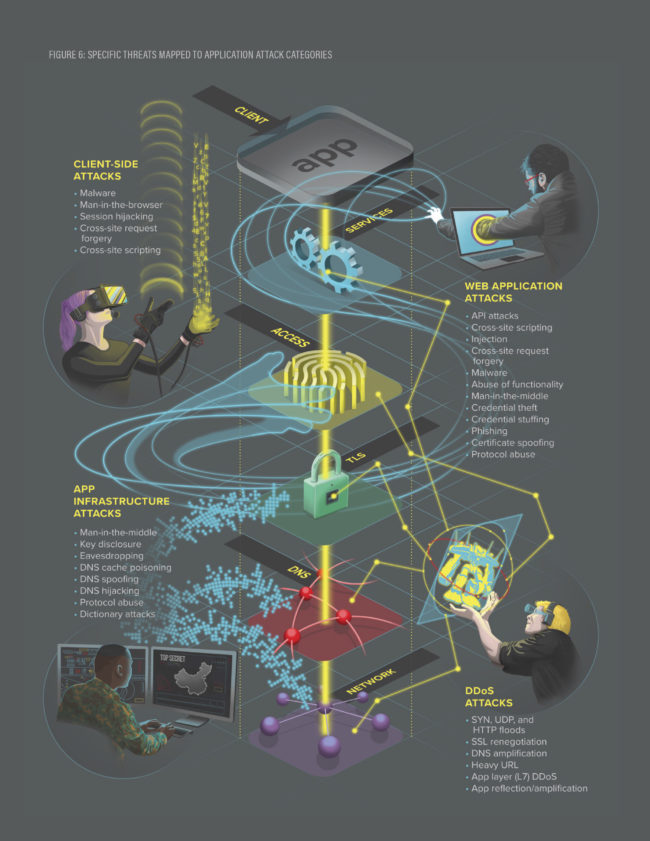
And since data is gold, applications are increasingly the target of cybercriminals. New research by F5 Labs found that web and applications attacks are the largest cause of security breaches (30 percent), with an average reported cost of close to US$8 Million per breach. It also found that a typical organization runs 765 web applications, with 34 percent of them considered mission-critical.
The research, using data gathered from Loryka and WhiteHat Security, provides analysis of the current threat landscape, detailed research stats and steps to secure applications to protect users and data.
Highlights from the F5 Labs’ Protecting Applications 2018 Report include:
Denial-of-service (DDoS) Attacks
- Credential theft, DDoS attacks, and web fraud are the top three attacks that are the most devastating to organizations represented in the global study.
- 69% of respondents in China and India are most concerned about DDoS attacks.
- APAC accounted for 17 percent of DDoS attacks in 2017, with a spike from Q4 2017 to Q1 2018.
- Security Response: DDoS attacks are pervasive across all levels of the application tier. It is critical that every organization has a DDoS response strategy.
Account Access Hijacking
- Breach records analysis shows that 13 percent of all web app breaches in 2017 and 1Q 2018 were access-related.
- Some of the top categories were:
- Credentials stolen via compromised email (34%)
- Access control misconfiguration (23%)
- Brute force attacks to crack passwords (5%)
- Credential stuffing from stolen passwords (9%)
- Social engineering theft (3%)
- Security Response: Stronger authentication solutions for mission-critical applications or for external applications over which organizations don’t have full control.
Injection Attacks
- Injection attacks allow an attacker to insert commands or new code directly into a running application with malicious intent.
- Injection vulnerabilities (weaknesses that have not yet been exploited) are prevalent. Those composed 17 percent of all discovered vulnerabilities in 2017.
- Security response: High priority should be given to finding, patching, and blocking injection vulnerabilities.
How likely are you to be hacked?
In general, there are two types of attackers: opportunists and targeted attackers:
- Opportunist attackers keep their ROI high by keeping costs low. They use a spray-and-pray approach to sweep the Internet looking for easy pickings. These attackers come at you with canned exploits and known methods. If rebuffed, they quickly move on to the next target.
- Targeted attackers choose their targets carefully. Their goal could be espionage or a high payoff, but it’s likely that once you’re in their sights, they’re coming after you. Though less prevalent, such attackers are generally more motivated
How can organizations improve application security?
Below are four low-difficulty steps:
- Understand your environment: Know what applications you have and what data repositories they access.
- Reduce your attack surface: Attackers will probe any part of an application service that is visible on the internet for possible exploitation.
- Prioritize defenses based on risk: Know which applications are important and minimize the attack surface by identifying applications that need additional resources.
- Select flexible and integrated defense tools: Have a good but manageable selection of flexible, powerful solutions to cover controls for prevention, detection, and recovery from existing and emerging threats.
Building a solid application defense strategy requires understanding each app and its areas of vulnerability, assigning an appropriate level of risk to the app according to the value of the data it contains, and taking a holistic view to securing applications based on their vulnerabilities, threats, and level of risk.
Read the full report to explore these core threat areas, understand their impact on apps in more detail, and obtain practical guidance on building an application defense strategy that works for your organization.