Nearly two-thirds (64%) of employees use a company-approved device for work. However, less than half (40%) of those who use a personal device are regulated when using that personal device, according to a new survey of 1,000 full-time employees published by Clutch, a B2B research firm.
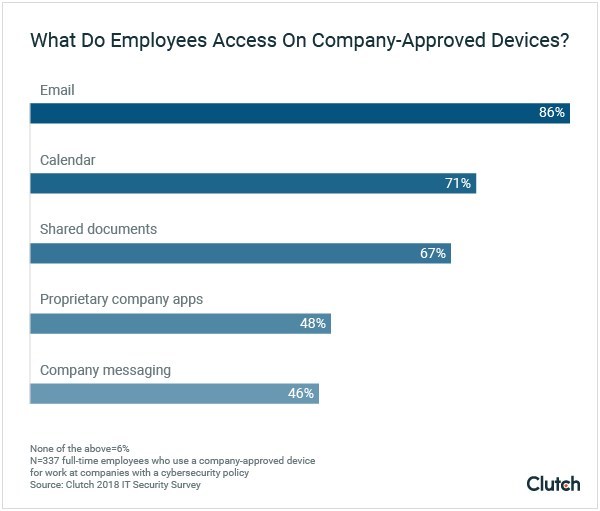
New data from Clutch reveals the work-related materials employees access on company-approved devices. (PRNewsfoto/Clutch)
Employees use personal devices for routine, daily work activities. Among those surveyed who use a personal device for work, 86% check their email and 67% access shared company documents.
“Normal,” or accepted employee behavior, often presents the most dangerous security threats, according to Randy Battat, CEO of PreVeil, a company that provides end-to-end encryption for email and file sharing.
“Employees believe that information that needs to be protected is special, sensitive stuff that’s explicitly marked and that most of the everyday communications they receive and send aren’t a risk for their organizations,” Battat said. “The reality is that the majority of communications and an organization’s intellectual capital can be found in the ‘ordinary’ email.”
Passwords Are the Front Line of Employee Security
Most employees use passwords as the primary form of IT security at their company. Over three-fourths (76%) practice some form of password protection, the survey found.
In addition, password update reminders are the most common cybersecurity policy employees encounter: Two-thirds (67%) of employees receive updates, followed by internet restrictions (55%) and user permission prompts (53%).
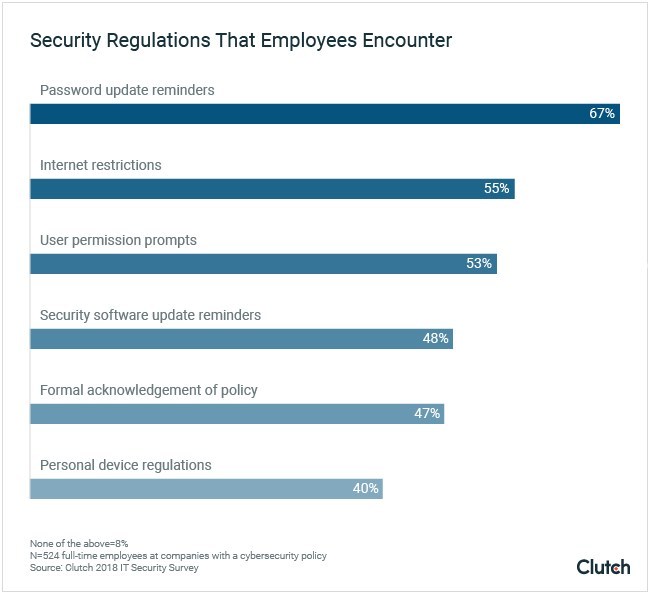
Clutch survey data shows security regulations employees regularly encounter at work. (PRNewsfoto/Clutch)
“[Employees] get that they have to change their password regularly because it’s an obvious protection. There’s a responsibility about that at an individual level,” said Steve Scott-Douglas, CIO of Ciklum, a software engineering and solutions company.
Most employees, however, use the simplest method of password protection: regularly updating their passwords. At least twice as many employees update passwords regularly (82%) compared to using complex password protection methods such as multi-factor authentication (41%) or a password manager (20%).
Employees Follow Cybersecurity Best Practices Beyond Company Policies
In several areas of cybersecurity, employees exhibit secure behavior that goes beyond their company’s policy.
For example, more employees report security incidents (60%) than go through cybersecurity policy or compliance training (59%).
This finding indicates that employees have a general understanding of IT security threats and best practices. However, without regular training or communication from their company, they may fail to recognize when they encounter security policy.
Most employees (52%) receive security policy training once per year, according to the survey.
The study suggested that to ensure employees recognize and comply with security policy, companies should implement consistent cybersecurity policy training.

















































































































