Menlo Security, a pioneer of cloud-based security isolation technology, announced a new phishing prevention solution expanding the Menlo Security Isolation Platform (MSIP) to stop email threats including malicious links, credential theft and weaponized attachments.
Majority of enterprise cybersecurity attacks begin through targeted email phishing attacks. These attacks spread from user end points to infect enterprise systems with malware that is subsequently leveraged to steal credentials, intellectual property and customer data. These breaches result in costs to the enterprise that range from millions to even billions of dollars in damages and tarnished reputation.
Current email security approaches, utilizing “good vs. bad” schemes to detect phishing and embedded malware, fail to stop targeted threats that can compromise thousands of users for weeks or even months before being recognized and removed. Existing security products simply fail to detect every malicious link and cannot protect every individual.
Further exacerbating this problem, legacy security solutions generate frequent incident alerts, requiring security professionals to continuously rule out false positives, resulting in severe strain on over-worked and understaffed cyber security teams.
The Menlo Security Phishing Isolation solution was developed in collaboration with Fortune 500 customers, to specifically address prevention shortfalls in existing secure email gateway products.
Available either on-premises, as-a-service via the cloud, or as part of a managed security service, the solution scales to address the needs of both large enterprise and smaller companies looking to eliminate phishing risk from their environments.
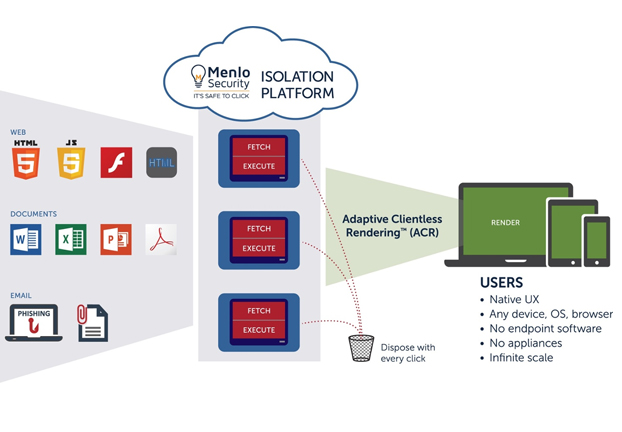
Menlo Security Phishing Isolation is integrated with existing email infrastructure including Exchange, Gmail and Office 365. By leveraging patented Adaptive Clientless Rendering (ACR) technologies, the solution enables enterprise-wide deployment of isolation security without the need to deploy or manage endpoint software, reducing risks without impacting the user experience.
The MSIP Phishing Isolation solution makes it safe for users to click on email links and attachments without the risk of infection from malware exploits. With this unique approach, users can safely view sites with input-field restrictions that eliminate credential theft, while providing configurable messages that enhance corporate phishing awareness training.
“Email persists as the top malware infection vector for enterprises, resulting in many forms of theft and fraud,” said Poornima DeBolle, co-founder and chief product officer of Menlo Security. “Adding phishing Isolation capabilities to the MSIP creates the only phishing prevention solution that completely eliminates targeted spear-phishing attacks and drive-by exploits by isolating all email links and attachments. By stopping this top infection vector, Menlo enables CISOs to report definitive progress against malware attacks to their boards of directors, while also freeing up precious cyber security incident-response resources within their teams.”