In 2013, a hacker group known to Kaspersky Lab as “Wild Neutron” (and which is also known as “Jripbot” and “Morpho”) attacked several high profile companies including Apple, Facebook, Twitter and Microsoft. After the incident was widely publicized, the threat actor went dark for almost a year. In late 2013 and early 2014, the attacks resumed and have continued in 2015.
The actor uses a stolen valid code verification certificate and an unknown Flash Player exploit. They use these to infect companies and private users around the world and steal sensitive business information.
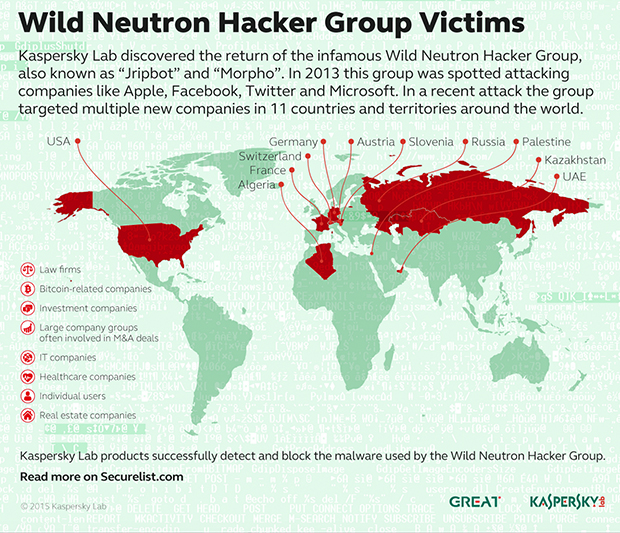
Kaspersky Lab researchers were able to identify targets of Wild Neutron in 11 countries and territories, including France, Russia, Switzerland, Germany, Austria, Palestine, Slovenia, Kazakhstan, UAE, Algeria and the United States. They include: law firms, Bitcoin-related companies, investment companies, groups of large companies often involved in M&A deals, IT companies, healthcare companies, real estate companies, and individual users.
The focus of the attacks suggests that this is not a nation-state sponsored actor. However, the use of zero-days, multi-platform malware as well as other techniques makes Kaspersky Lab researchers believe it’s a powerful entity engaged in espionage, possibly for economic reasons.
The initial infection vector of the recent attacks is still unknown, although there are clear indications that victims are exploited by a kit that leverages an unknown Flash Player exploit through compromised websites. The exploit delivers a malware dropper package to the victim.
In the attacks observed by Kaspersky Lab researchers, the dropper was signed with a legitimate code verification certificate.
The use of certificates allows malware to avoid detection by some protection solutions. The certificate used in the Wild Neutron attacks appears to be stolen from a popular manufacturer of consumer electronics. The certificate is now being revoked.
After getting in the system, the dropper installs the main backdoor.
In terms of functionality, the main backdoor is no different to many other Remote Access Tools (RATs). What really stands out is the attacker’s care in hiding the command and control server (C&C) address and its ability to recover from a C&C shutdown.
The command and control server is an important part of the malicious infrastructure as it serves as a “homebase” for the malware deployed on victims’ machines. Special measures built into the malware help the attackers to protect the infrastructure from any possible C&C-takedowns.
The origin of the attackers remains a mystery. In some of the samples, the encrypted configuration includes the string “La revedere” (“Goodbye” in Romanian) to mark the end of the C&C communication.
In addition to that, Kaspersky Lab researchers have found another non-English string which is the Latin transcription of the Russian word “Успешно” (“uspeshno” -> “successfully”).
“Wild Neutron is a skilled and quite versatile group. Active since 2011, it has been using at least one zero-day exploit, custom malware and tools for Windows and OS X. Even though in the past it has attacked some of the most prominent companies in the world, it has managed to keep a relatively low profile via solid operational security which has so far eluded most attribution efforts,” said Costin Raiu, director for global research and analysis team at Kaspersky Lab. “The group’s targeting of major IT companies, spyware developers (FlexiSPY), jihadist forums (the ‘Ansar Al-Mujahideen English Forum’) and Bitcoin companies indicate a flexible yet unusual mindset and interests.”
Kaspersky Lab products detect and block the malware used by the Wild Neutron threat actor with the following detection names: Trojan.Win32.WildNeutron.gen, Trojan.Win32.WildNeutron., Trojan.Win32.JripBot., and Trojan.Win32.Generic.
More information about the Wild Neutron attribution is available to Kaspersky Intelligence Services customers. Contact: intelreports@kaspersky.com.