Trend Micro researchers have discovered MalumPoS, a new PoS attack tool that threat actors can reconfigure to breach any PoS system they wish to target. Currently, it is designed to collect data from PoS systems running on Oracle MICROS – a platform popularly used in the hospitality, food and beverage, and retail industries and is claimed by Oracle to be used in 330,000 customer sites worldwide.
As highlighted in Trend Micro’s recent Q1 report “Bad Ads and Zero-Days: Reemerging Threats Challenge Trust in Supply Chains and Best Practices”, PoS malware and tools have become one of the biggest issues and concerns in the security industry with PoS RAM scrapers continuing to increase in number.
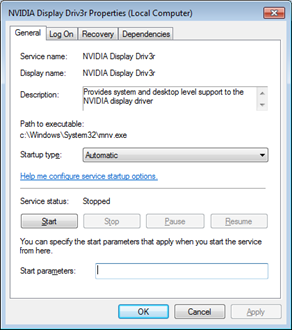
Compared to other PoS RAM scrapers seen in the past, this particular MalumPoS threat shows a few interesting characteristics and noteworthy details.
Aside from Oracle MICROS, MalumPoS also targets Oracle Forms, Shift4 systems, and those accessed via Internet Explorer. Based on the user base of these listed platforms, a majority were from the US.
Once installed in a system, MalumPoS disguises itself as “the “NVIDIA Display Driver” or stylized to be displayed as “NVIDIA Display Driv3r”. Although typical NVIDIA components play no important parts in PoS systems, their familiarity to regular users may make the malware seem harmless.
It selectively looks for any data on the following cards: Visa, MasterCard, American Express, Discover, and Diner’s Club.
MalumPoS is highly configurable so a threat actor can still change or add to this current list of targeted systems and credit card targets.