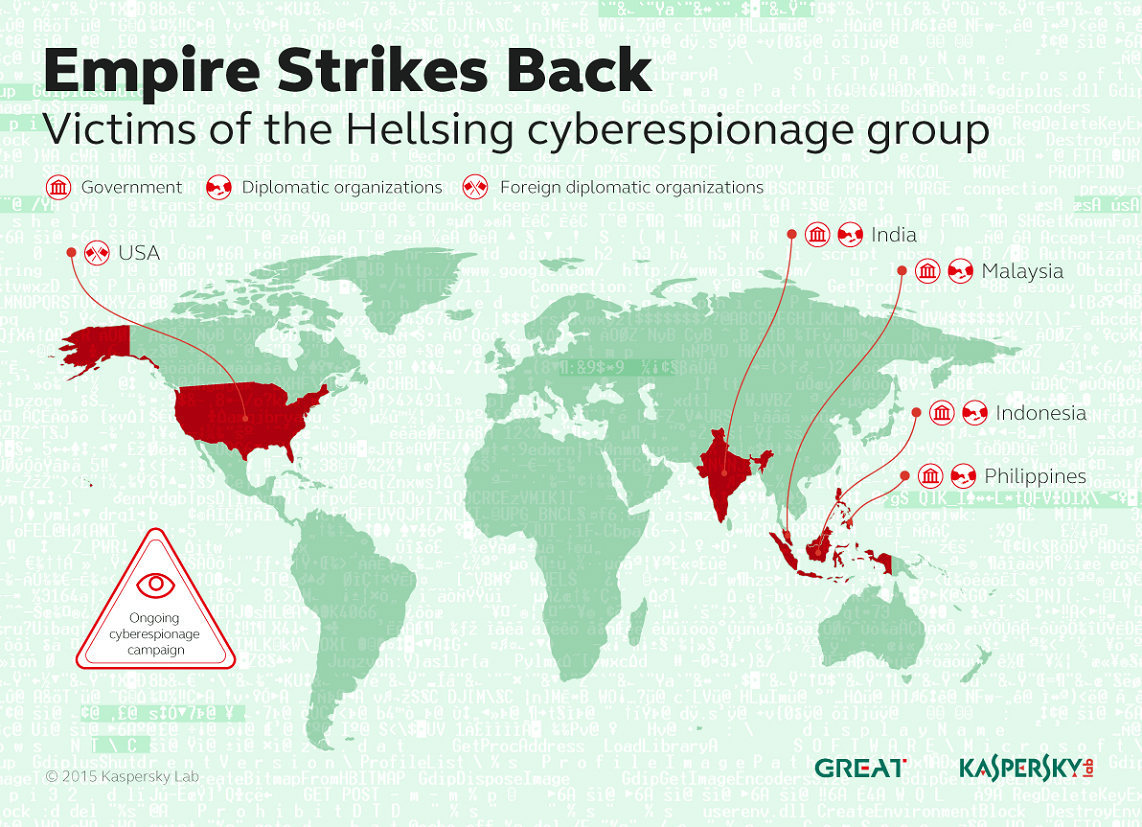
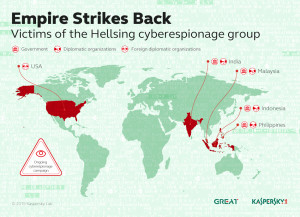
Close to 20 organizations, mostly government and diplomatic entities, are targeted by the Hellsing malware, which has been active since at least 2012 and remains active, according to Kaspersky Lab.
The company has detected and blocked the Hellsing malware in Malaysia, the Philippines, India, Indonesia and the US, with most of the victims located in Malaysia and the Philippines.
The Hellsing malware is involved in a new cybercriminal activity dubbed as “the advanced persistent threats (APT) wars” where cybercriminal groups attack each other.
APTs are hacking activities, which usually target organizations and are designed to steal big data and business secrets.
Involving Hellsing and Naikon cyberespionage groups, the emerging activity was discovered by Kaspersky when the latter subjected the former to a spear-phishing attack. Naikon attempted to infect Hellsing’s systems with an email containing a malicious attachment.
Hellsing received the email, questioned its authenticity with the sender but was dissatisfied with the reply and didn’t open the attachment. In response, it returned the email to Naikon carrying with it its own malware.
Hellsing’s counter-attack points out that it wanted to identify the Naikon group and gather intelligence on it.
The tracking made by Kaspersky reveals that the spear-phishing emails with malicious attachments were designed to propagate espionage malware among different organizations to keep tract on them.
In this cybercriminal activity, once a malicious attachment is opened, the system becomes infected with a custom backdoor capable of downloading and uploading files, updating and uninstalling itself.
 “The targeting of the Naikon group by Hellsing, in some sort of a vengeful vampire-hunting “Empire Strikes Back” style, is fascinating. In the past, we’ve seen APT groups accidentally hitting each other while stealing address books from victims and then mass-mailing everyone on each of these lists. However, considering the targeting and origin of the attack, it seems more likely that this is an example of a deliberate APT-to-APT attack,” said Costin Raiu, Director of Global Research and Analyst Team at Kaspersky Lab.
“The targeting of the Naikon group by Hellsing, in some sort of a vengeful vampire-hunting “Empire Strikes Back” style, is fascinating. In the past, we’ve seen APT groups accidentally hitting each other while stealing address books from victims and then mass-mailing everyone on each of these lists. However, considering the targeting and origin of the attack, it seems more likely that this is an example of a deliberate APT-to-APT attack,” said Costin Raiu, Director of Global Research and Analyst Team at Kaspersky Lab.
To protect against Hellsing and Naikon attacks, Kaspersky Lab has products that successfully detect and block malware employed by these actors.
Meanwhile, Vicente Diaz, Principal Security Researcher at Kaspersky Lab’s Global Research and Analysis Team, said that in the Philippines, Kaspersky Lab is processing 315,000 unique malware samples every single day.
Diaz cited that the most prominent mobile malware is Android which comprised 98.05%, followed by J2MC, 1.55%, and SymbOS, 0.27%.
For the first quarter of 2015, the Philippines hosted 6,043 incidents of malware attacks, placing it 78th on the global scene.
Forty-four percent of local users were attacked by some malware, placing it 47th worldwide. Web malware, on the other hand, affected 19.6% of users.