Kaspersky Lab’s Global Research and Analysis Team has published its research on Regin – the first cyber-attack platform known to penetrate and monitor GSM (Global System for Mobile communications) networks in addition to other “standard” spying tasks.
The attackers behind this platform have compromised computer networks in at least 14 countries around the world.
The main victims of this actor are: telecom operators, governments, financial institutions, research organizations, multinational political bodies and individuals involved in advanced mathematical/cryptographical research.
Victims of this actor have been found in Algeria, Afghanistan, Belgium, Brazil, Fiji, Germany, Iran, India, Indonesia, Kiribati, Malaysia, Pakistan, Syria and Russia.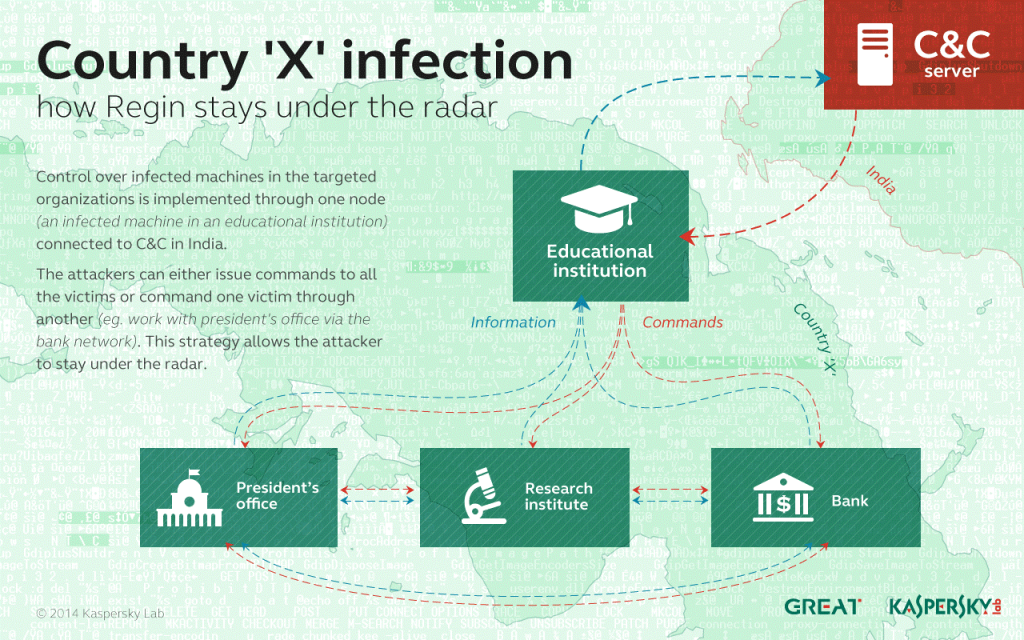
The Regin platform consists of multiple malicious tools capable of compromising the entire network of an attacked organization. It uses an incredibly complex communication method between infected networks and command and control servers, allowing remote control and data transmission by stealth.
One particular Regin module is capable of monitoring GSM base station controllers, collecting data about GSM cells and the network infrastructure.
Over the course of a single month in April 2008 the attackers collected administrative credentials that would allow them to manipulate a GSM network in a Middle Eastern country.
Some of the earliest samples of Regin appear to have been created as early as 2003.
In 2012, Kaspersky Lab experts became aware of Regin malware, which seemed to belong to a sophisticated espionage campaign.
For almost three subsequent years Kaspersky Lab’s experts tracked this malware all over the world. From time to time, samples would appear on various multi-scanner services, but they were all unrelated to each other, cryptic in functionality and lacking context.
However, Kaspersky Lab experts were able to obtain samples involved in several real world attacks, including those against governmental institutions and telecom operators, and this provided enough information to research more deeply into this threat.
That in-depth study found that Regin is not just a single malicious program, but a platform – a software package, consisting of multiple modules, capable of infecting the entire networks of targeted organizations to seize full remote control at all possible levels.
Regin is aimed at gathering confidential data from attacked networks and performing several other types of attacks.
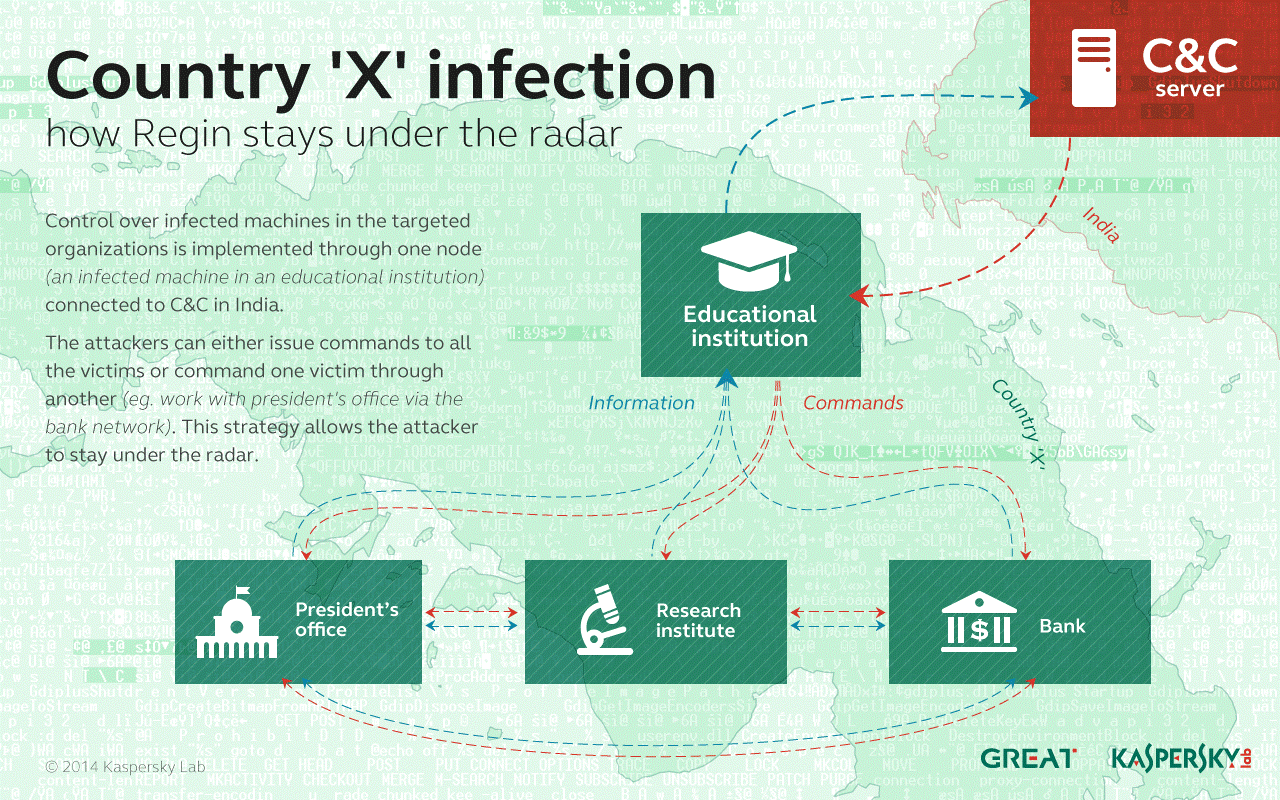
The actor behind the Regin platform has a well-developed method to control the infected networks.
Kaspersky Lab experts observed several compromised organizations in one country, but only one of them was programmed to communicate with the command and control server located in another country.
However all the Regin victims in the region were joined together in a peer to peer VPN-like network and able to communicate with each other.
Thus, attackers turned compromised organizations in one vast unified victim and were able to send commands and steal the information via a single entry point.
According to Kaspersky Lab’s research this structure allowed the actor to operate silently for years without raising suspicions.
The most original and interesting feature of the Regin platform, though, is its ability to attack GSM networks.
According to an activity log on a GSM Base Station Controller obtained by Kaspersky Lab researchers during the investigation, attackers were able to obtain credentials that would allow them to control GSM cells in the network of a large cellular operator.
This means that they could have had access to information about which calls are processed by a particular cell, redirect these calls to other cells, activate neighbor cells and perform other offensive activities.
At the present time, the attackers behind Regin are the only ones known to have been capable of doing such operations.
“The ability to penetrate and monitor GSM networks is perhaps the most unusual and interesting aspect of these operations. In today’s world, we have become too dependent on mobile phone networks which rely on ancient communication protocols with little or no security available for the end user,” said Costin Raiu, Director of Global Research and Analysis Team at Kaspersky Lab.
“Although all GSM networks have mechanisms embedded which allow entities such as law enforcement to track suspects, other parties can hijack this ability and abuse it to launch different attacks against mobile users,” Raiu added.