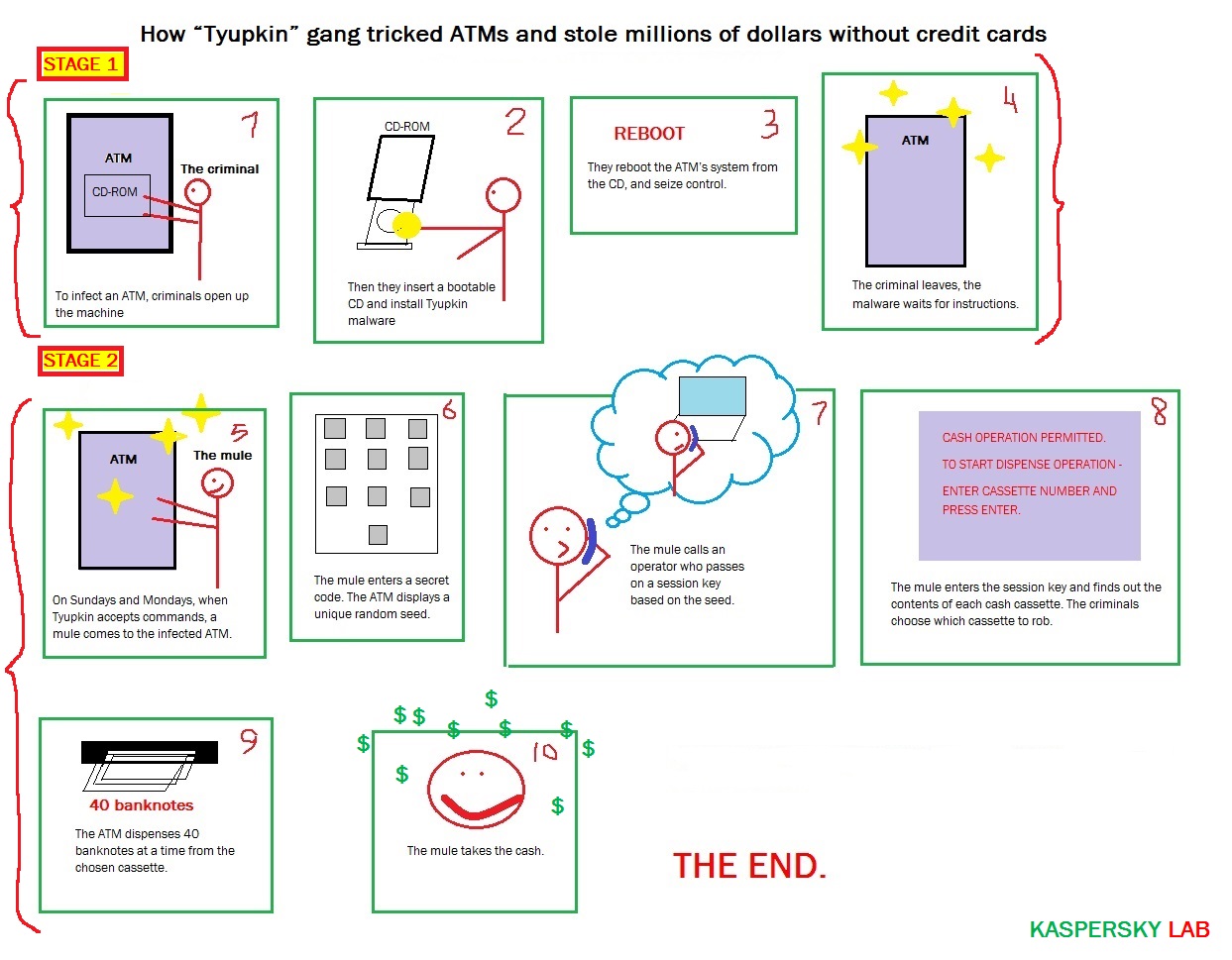
Without inserting a credit card into the ATM slot, a gang of cybercriminals enter a combination of digits on the ATM’s keyboard, make a call to receive further instructions from an operator, enter another set of numbers and the ATM starts giving out cash, lots of cash. Then they leave.
The attack was discovered by Kaspersky Lab‘s experts which performed a forensic investigation into cyber-criminal attacks targeting multiple ATMs around the world.
During the course of this investigation, the company’s researchers discovered a piece of malware infecting ATMs that allowed attackers to empty the cash machines via direct manipulation, stealing millions of dollars. INTERPOL alerted the affected member countries and is assisting ongoing investigations.
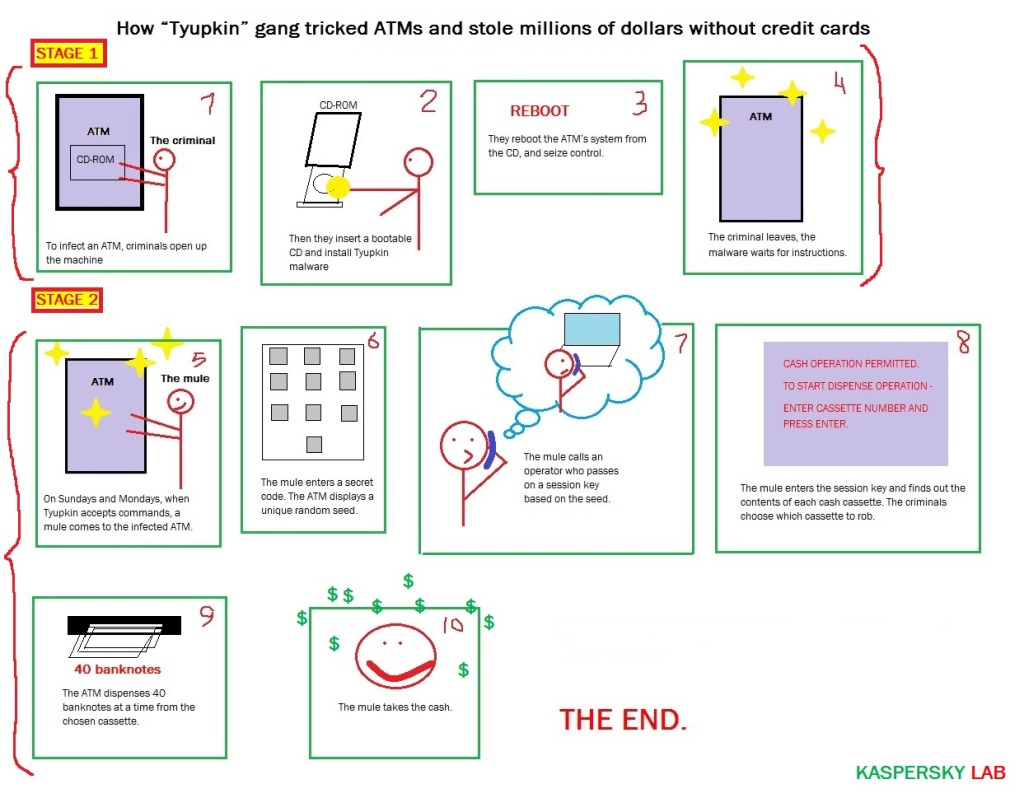 According to Kaspersky, the criminals work in two stages. First, they get physical access to the ATMs and insert a bootable CD to install the malware – code named Tyupkin by Kaspersky Lab. After they reboot the system, the infected ATM is under their control.
According to Kaspersky, the criminals work in two stages. First, they get physical access to the ATMs and insert a bootable CD to install the malware – code named Tyupkin by Kaspersky Lab. After they reboot the system, the infected ATM is under their control.
After a successful infection, the malware runs in an infinite loop waiting for a command. To make the scam harder to spot, Tyupkin malware only accepts commands at specific times on Sunday and Monday nights. During those hours the attackers are able to steal money from the infected machine.
Video Footage obtained from security cameras at the infected ATMs showed the methodology used to access cash from the machines.
A unique digit combination key based on random numbers is freshly generated for every session. This ensures that no person outside the gang could accidentally profit from the fraud.
Then the malicious operator receives instructions by phone from another member of the gang who knows the algorithm and is able to generate a session key based on the number shown. This ensures that the mules collecting the cash do not try to go it alone.
When the key is entered correctly, the ATM displays details of how much money is available in each cash cassette, inviting the operator to choose which cassette to rob.
After this the ATM dispenses 40 banknotes at a time from the chosen cassette.
The Tyupkin Malware
At the request of a financial institution, Kaspersky Lab’s Global Research and Analysis Team performed a forensic investigation into this cyber-criminal attack, The malware identified and named by Kaspersky Lab as Backdoor.MSIL.Tyupkin, has so far been detected on ATMs in Latin America, Europe and Asia.
“Over the last few years, we have observed a major upswing in ATM attacks using skimming devices and malicious software. Now we are seeing the natural evolution of this threat with cyber-criminals moving up the chain and targeting financial institutions directly. This is done by infecting ATMs themselves or launching direct APT-style attacks against banks. The Tyupkin malware is an example of the attackers taking advantage of weaknesses in the ATM infrastructure,” said Vicente Diaz, Principal Security Researcher at Kaspersky Lab’s Global Research and Analysis Team.
“We strongly advise banks to review the physical security of their ATMs and network infrastructure and consider investing in quality security solutions,” Diaz added.
“Offenders are constantly identifying new ways to evolve their methodologies to commit crimes, and it is essential that we keep law enforcement in our member countries involved and informed about current trends and modus operandi,” said Sanjay Virmani, Director of the INTERPOL Digital Crime Centre.
What banks can do to mitigate the risk:
– Review the physical security of their ATMs and consider investing in quality security solutions.
– Replace all locks and master keys on the upper hood of the ATM machines and ditch the defaults provided by the manufacturer.
– Install an alarm and ensure it is in good working order. The cyber-criminals behind Tyupkin only infected ATMs that had no security alarm installed.
– Change the default BIOS password.
– Ensure the machines have up-to-date antivirus protection