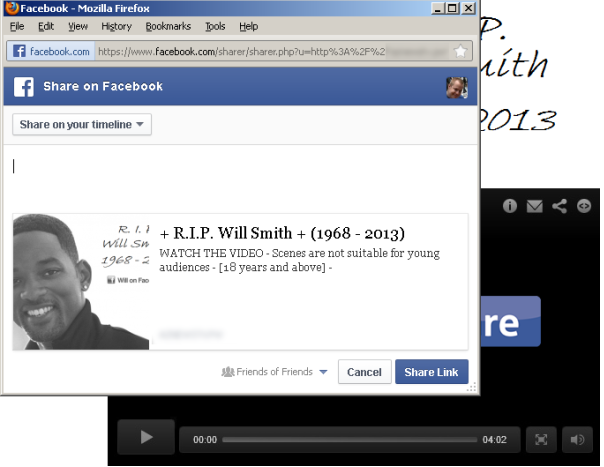
The rise of “rest in peace” scam messages on social media sites continues, warns Symantec. Jackie Chan, Morgan Freeman, Will Smith, Keanu Reeves, and Rihanna are only a few of the celebrities that have been proclaimed dead in recent scams.
The sensational messages usually include links to a video. Before the user gets to see the video, they are tricked into manually sharing the bait message with all of their family and friends in order to spread the scam further. Even after sharing the post, the user will still not be able to see the fake video. Rather, they will be redirected to a site with advertisements that asks the user to fill out a survey. The ads and surveys generate revenue for the scammer. Other variants of the scam ask the user to download a malicious browser extension or application. This kind of scam is not new, but as long as they make money, they will continue.
Some scammers are currently focusing on Paul Walker and Roger Rodas, who both recently died in a car accident. Even though the base of the story is true, the scammers are using these tragic deaths to try to promote fake videos which claim to include unseen footage of the crash. One scam group has specialized in the use of malicious Facebook applications to boost the reach of the scam. With a simple geo IP location JavaScript, the scammers can determine the user’s location and redirect their browser to a site that suits their region. This is straight forward and common behavior nowadays. The redirects can point to malicious Facebook apps, remotely hosted scams sites, or phishing sites. Luckily, in this example, the phishing website does not look very convincing, as some browsers break the layout of the site.
Unfortunately, the redirects can sometimes skip one of Facebook’s warnings about malicious URLs. Whenever a user clicks on a link in a Facebook post, the browser will get redirected to a transfer script. If Facebook thinks that the destination URL is suspicious, a warning message is displayed, informing the user and allowing them to report the post as spam. Since the Web page is shown in an iframe below the warning, it is possible, in some rare cases, that the scammer could automatically redirect the user to a new site. As a result, the user will only see the warning message for less than a second before they are sent to the malicious Facebook application page. Often, multiple redirects are involved until the final page is reached.
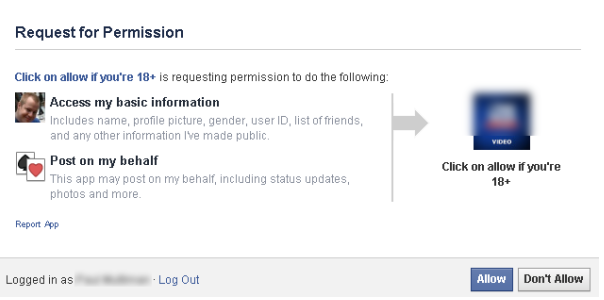
If a user attempts to install a malicious application, the app asks for permission to read the user’s data and to post in their timeline. The scammer’s main goal here is to post the message through the user’s Facebook account without the victim’s knowledge so that more people fall for the scam. Once the user installs the application, the scam message is posted to their timeline and the user is redirected to the survey scam Web pages.
A few hundred people per hour have clicked on each of these links and some have installed the application.
Of course, Facebook is doing its best to block the malicious links and remove the applications as fast as possible. Unfortunately the bad guys have automated scripts on their side. Each of the analyzed domains hosted more than 2,000 copies of the malicious Facebook application, each under a slightly different name.
This allows the scammers to rotate the malicious links once the app is blocked.
As always, Internet users are advised to follow best practices:
• Be vigilant and skeptical when reading sensational stories on social media sites
• Do not install plugins or tools from untrusted sites
• Think twice before filling out verification surveys in order to access content
• When installing social applications, verify that the requested permissions are really required