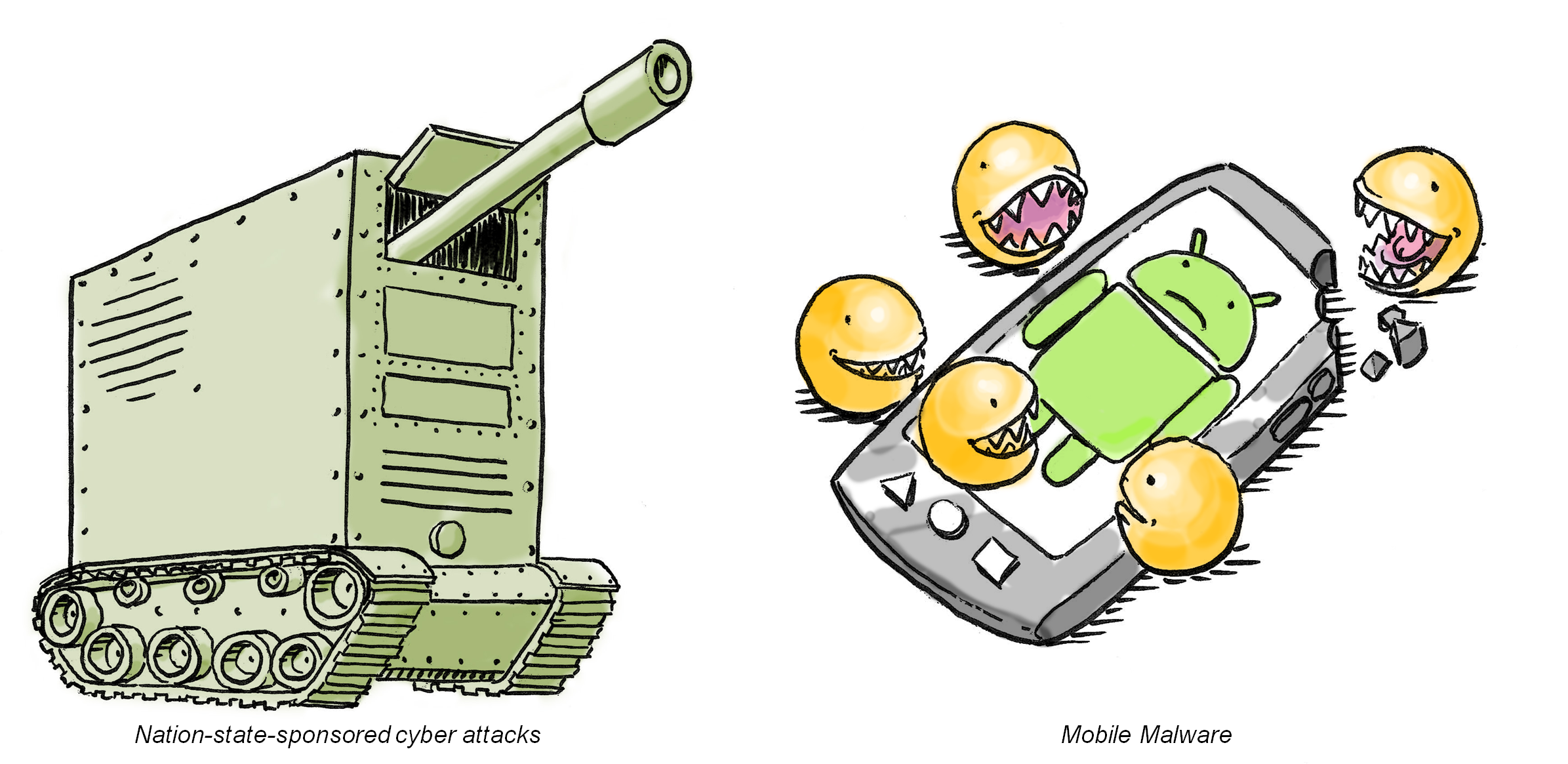
The first three months of the year turned out to be full of incidents, especially when it came to cyber espionage and cyber weapons, according to Kaspersky Lab’s latest report called IT Threat Evolution: Q1 2013.
Among the most persistent cyber espionage network was the global operation known as Red October, which targeted various government offices, diplomatic offices and companies worldwide.
Among the most persistent cyber espionage network was the global operation known as Red October, which targeted various government offices, diplomatic offices and companies worldwide.
Kaspersky Lab reported that Red October has been active for at least five years and have expanded their network of infected systems over 60 domain names spread across several host servers across the world.
Red October’s techniques have also expanded to infecting and stealing through USB devices and smartphones.
Another group, APT1 (Advanced Persistent Threat), allegedly composed of Chinese hackers, has also become a major threat.
Kaspersky Lab cited a report from cyber-security company Mandiant that emphasized APT1 has been operating since 2006 and has since managed to steal huge amounts of data from around 141 organizations.
Kaspersky Lab also noted that these massive attacks could not be possible without real support from hundreds of people and a developed, modern infrastructure.
Denis Maslennikov, Kaspersky Lab Security Expert and author of the report, said that, China has faced accusations of its involvement in cyber attacks against government agencies and organizations in countries around the world.
“There is nothing particularly surprising about the Chinese government’s firm rejection of the assertions made in the Mandiant report,” Maslennikov added.
Another group called TeamSpy has been seen to target high-ranking politicians and human rights advocates in Eastern Europe and commonwealth of independent states (CIS). While not as sophisticated as other cyber attackers, many of the attacks from TeamSpy were mostly successful.
It also reported that there were cyber attacks against Tibetan and Uyghur activists. The perpetrators used Mac OS, Windows, and Android as platforms for these targeted attacks.
Mobile threats
Kaspersky Lab reported that mobile threats have also been increasing with Android as a leading target platform.
Over the last three months, Kaspersky Lab has found 20,000 new modifications of popular mobile malware. This is nearly half of what KSN found in the whole of 2012.
Kaspersky Lab added that 99.9 percent of all new mobile threat detections targeted the Android operating system.
SMS Trojans are still the most prevalent category of mobile threats accounting for 63.6 percent of all attacks. Among the most dangerous programs for Android are FakeInst, Plangton, Opfake, Agent, AveaSMS, Walien, Trackplus, Copycat, Fav, Penetho, SMSReg, and FaceNiff.
Kaspersky Lab also found new mobile malware called Perkel, a banking Trojan and MTK Botnet, which has allegedly infected over one million Android devices mostly in China.
“The number of apps for Android is constantly on the rise, and it is often a challenge to gain popularity with users — which is why these illegitimate tactics are becoming all the more common,” said Maslennikov.
Statistics on attacks
The report noted that at least 1.3 billion threats were detected and neutralized by Kaspersky Lab. It also indicated that the US (25.1 percent) remained as the most targeted country used to seed malware, followed by Russia (19.2 percent), The Netherlands (14.4 percent), Germany (11.5 percent), Ukraine (3.3 percent), and Great Britain (3.0 percent). Other countries only contributed around 1.8 percent or less.
Countries with the highest risk of infection from malware is topped by Tajikistan followed by Armenia, Russia , Kazakhstan, Azerbaijan, Moldova, Belarus, Ukraine, Uzbekistan, Kyrgyzstan, Vietnam, Georgia, Tunisia, Sri Lanka, Greece, Italy, India, Algeria, Lithuania, and Latvia.
Likewise, KSN said that there are countries considered “safe zones” against malware infection. These are Japan, Denmark, Finland, Sweden, the Czech Republic, Switzerland Ireland, The Netherlands, New Zealand, and Norway.
Fight against mobile malware, cyber espionage
Jimmy Fong, Channel Sales Director for Kaspersky Lab Southeast Asia said that while the Philippines seems relatively safe from major mobile malware and cyber espionage, he warned that attacks against government institutions and corporations is possible.
He added that recent news reports of massive denial-of-service (DDOS) attacks against a number of government websites could be used as indicators of what could possibly happen.
“These attacks can be dangerous for any institution especially now that the Philippines is linked to other countries via broadband Internet connections. Security even in the virtual world is the responsibility of everyone and putting in place the best security solutions is paramount,” according to Fong.